 Sign in
Sign in
Technology
Business
Christophe Foulon
Let's advance your cybersecurity career.
I strive to shine a light on the value of others so they can see it in themselves.
I provide a tailored cybersecurity performance-based coaching program focused on the individual needs of each client and delivering results.
I offer career coaching services through cpf-coaching.com I offer an introductory session to see if my services are a right fit for your goals you can book a session here https://calendar.app.google/EHC1SKeiwDq3ESYp8 substack.cpf-coaching.com

NetFlow Analysis: A Game-Changer for SMB Network Security and Efficiency
Small and medium-sized businesses (SMBs) often struggle with network security. The landscape can feel overwhelming, especially with limited budgets, constrained resources, and the need to wear multiple hats. Many SMBs view advanced security tools as out of reach and reserved for large organizations with expansive budgets and dedicated teams. However, NetFlow is a hidden gem within reach of most businesses.SMB Tech & Cybersecurity Leadership Newsletter is a reader-supported publication. To receive new posts and support my work, consider becoming a free or paid subscriber.NetFlow is like having a security camera on your network. Still, instead of capturing visual data, it records the conversations happening within your network—who’s talking to whom, when, and what information is being exchanged. This network protocol collects IP traffic data flowing through your routers and switches, allowing you to monitor and analyze your network in real-time. With the right tools, NetFlow transforms this data into actionable insights, allowing you to proactively identify unusual patterns and address potential threats.Imagine a scenario where your business experiences a sudden website crash. This might be due to a Distributed Denial of Service (DDoS) attack. NetFlow analysis can help you detect such attacks early by identifying unusual traffic spikes from malicious IP addresses, enabling you to mitigate the threat before it disrupts your operations. Similarly, NetFlow can highlight subtle signs of data breaches, like unusual data transfers to unknown locations, even during off-hours.One of NetFlow's most compelling aspects is its accessibility for SMBs. Unlike many high-cost solutions, NetFlow leverages existing network infrastructure, making it cost-effective. Most modern routers and switches already support it, so there’s no need for expensive hardware upgrades.Beyond security, NetFlow offers operational benefits. It provides insights into bandwidth usage, application performance, and network bottlenecks, enabling you to optimize your network and plan for future growth. Additionally, its ability to integrate seamlessly with tools like Security Information and Event Management (SIEM) systems creates a unified security ecosystem, enhancing threat detection and response.For SMBs looking to get started with NetFlow, the first step is to assess your network infrastructure for compatibility. Begin by monitoring critical network segments, such as servers with sensitive data, and invest in training for your IT team to ensure they can interpret NetFlow data effectively. Consider your specific security and operational goals when choosing a tool that balances functionality, ease of use, and affordability.NetFlow empowers SMBs to improve their security, enhance network performance, and gain a competitive edge. It’s an essential tool in today’s cybersecurity landscape—powerful, accessible, and transformative. The journey begins with a single step: check your infrastructure, train your team, and start leveraging NetFlow's power.A Caveat for SMBs Using Cloud ServicesFor SMBs relying heavily on cloud services or Infrastructure as a Service (IaaS) platforms, NetFlow analysis might not fully apply. Many cloud providers do not offer granular access to traffic flow data at the level required for NetFlow analysis. Instead, these organizations might need to rely on the cloud provider’s monitoring tools and security features. If this applies to you, it’s essential to understand what visibility and controls your cloud provider offers and explore complementary solutions.Thanks for reading SMB Tech & Cybersecurity Leadership Newsletter! If you found value in this post, feel free to share it.Product shoutout: TenableCPF Coaching Recommends Tenable for your vulnerability scanning needs. Proactive vulnerability management is crucial to your organization's healthy hygiene.Check it out here: https://shop.tenable.com/cpf-coachingCyvatar.aiHow often do you track the maturity of your program or the implementation status of your controls? As an SMB, it can sometimes be hard to access cybersecurity assessments and tooling; here is a self-assessment tool that you can use to see where your business stands.If you are looking for a security resource to help guide you through the assessment or the maturation of your security program.See where your program scores https://cyvatar.ai/cybersecurity-self-assessment/?via-rr=CHRISTOPHE77 This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
02:3315/11/2024

Maximizing Cybersecurity for SMBs: The Power of Alerting Systems
Maximizing Cybersecurity for SMBs: The Power of Alerting SystemsAs a senior cybersecurity leader and advisor, I've witnessed firsthand the evolving landscape of digital threats facing small and medium-sized businesses (SMBs). In today's interconnected world, cybersecurity is no longer a luxury but a necessity for businesses of all sizes. The rapid digitalization of operations, coupled with the increasing sophistication of cyber attacks, has made it imperative for SMBs to implement robust security measures. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
07:0708/11/2024

Essential Cybersecurity Tips for Small Businesses in 2024
Cybercriminals are progressively targeting small businesses. Implementing strong cybersecurity measures is essential to safeguarding your business. This guide provides a thorough overview of how to help protect your small business from cyber threats in 2024. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
12:2831/10/2024

Securing Remote Workforces: Best Practices for SMBs
Learn the best practices for securing remote workforces, including implementing strong security policies, enhancing team-wide cybersecurity, and securing home networks. Protect your SMB from cyber threats with these expert insights.Subscribe for future episodes! This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
03:5622/10/2024

Enabling SMBs to understand and address Insider Threats in their businesses
Small and Medium-sized Businesses (SMBs) face numerous security challenges, with insider threats ranking among the most damaging but often undiscussed; with the right strategies and a proactive approach, these threats can be effectively mitigated. Insider threats arise from individuals within an organization who abuse their access to sensitive information or systems for unauthorized purposes and harm the company, intentionally or unintentionally. These threats can lead to data breaches, financial losses, reputational damage, and operational disruptions. Unlike external cyber-attacks, insider threats are more challenging to detect because the individuals involved already have authorized access to sensitive resources. Let's explore the growing concern of insider threats in SMBs and offer practical strategies to mitigate them, with the potential for success and a more secure future for your business.1. Introduction to Insider Threats in SMBsDefining Insider ThreatsAn insider threat occurs when someone authorized access to a company's systems and data misuses that privilege, maliciously or unintentionally, to harm the organization. This threat can come from current or former employees, contractors, or business partners with legitimate access to sensitive resources. In small and medium-sized businesses (SMBs), insider threats are particularly worrisome because these businesses often have fewer layers of security than larger enterprises. Employees in SMBs may have broader access to systems, which increases the risk of misuse. Insider threats can significantly impact a company's success, leading to severe consequences such as data breaches, financial losses, reputational damage, and operational disruptions. Whether the intent is to steal data, sabotage operations, or unintentionally expose sensitive information, the effects of insider threats can be devastating.The Growing Concern for SMBsRecent cybersecurity reports, such as one from the Ponemon Institute, indicate that insider threats have grown by nearly 50% over the past few years. This trend is alarming, particularly for SMBs, which often lack the sophisticated security infrastructure of larger organizations. These larger organizations might have dedicated security teams, advanced threat detection systems, and regular security audits, which SMBs may need more resources to implement. The smaller teams and limited resources of SMBs make it challenging to implement comprehensive security measures, leaving them more vulnerable to insider attacks. Additionally, SMBs may only sometimes have dedicated IT staff to monitor security threats in real-time. With the rise of remote work and increased digital reliance, insider threats are becoming an even more pressing issue for small businesses.2. Mitigating Employee-Related RisksIdentifying Potential RisksThe first step in addressing insider threats is identifying the potential risks that employees may pose. Common risk factors include disgruntled employees who may be motivated to harm the business, accidental data leaks due to negligence, and weak access control policies that give too much access to sensitive information. SMBs can reduce these risks by employing behavioral monitoring technologies that track abnormal employee activities. For example, unusual login times, unauthorized file access, or abnormal data transfers can serve as red flags. Identifying these risks early on enables SMBs to take proactive steps before damage occurs.Implementing Preventative MeasuresSmall and medium-sized businesses (SMBs) need to establish and enforce strong preventive measures to minimize the risk of insider threats. Implementing strict access control policies is one of the most effective methods for protecting sensitive data. These policies should follow the principle of least privilege, meaning that employees should only have access to the data and systems necessary for their specific roles. This principle ensures that even if an employee's credentials are compromised, the potential damage is limited to the data and systems they access, reducing the overall risk. It's crucial to regularly review and update these access controls to prevent employees from retaining unnecessary permissions after role changes. Additionally, businesses need to conduct thorough background checks on new hires, closely monitor employee activities for any signs of suspicious behavior, and ensure the encryption of sensitive data to prevent unauthorized access.3. Insider Threat Identification TechniquesBehavioral Monitoring TechnologiesBehavioral monitoring technologies are crucial in identifying insider threats; these technologies monitor and analyze employee activities, including email communications, network access, file transfers, and login patterns. For instance, sudden access to large volumes of sensitive data or downloading files outside of regular business hours could indicate an insider threat. However, small and medium-sized businesses (SMBs) must balance these technologies with privacy concerns by ensuring employees are aware of the monitoring while safeguarding their data. It's important to note that while these tools are powerful, they are not infallible and may sometimes produce false positives that require careful interpretation.Early Detection StrategiesEarly detection of insider threats is critical to limiting potential damage. Anomaly detection systems, user behavior analytics (UBA), and machine learning algorithms are powerful tools that can flag suspicious activities before they escalate into major incidents. These tools establish a baseline of normal behavior for each employee and then detect deviations that may signal malicious intent or accidental data exposure. For example, an anomaly detection system could identify employees accessing customer data they usually wouldn't, prompting a deeper investigation. SMBs that deploy these strategies can reduce the risk of significant financial or reputational harm by catching threats in their early stages.4. Effective Access Control PoliciesDeveloping Robust PoliciesSmall and medium-sized businesses (SMBs) must establish effective access control policies to safeguard sensitive information. The following guidelines dictate which employees can access particular data, ensuring access is only given to those needing it for their specific roles. Small and medium-sized businesses (SMBs) should focus on implementing role-based access control (RBAC) systems, where permissions are based on the employee's job function rather than their seniority or length of employment. This approach reduces the risk of unauthorized access. Additionally, these policies should include multi-factor authentication (MFA), which necessitates employees to confirm their identity through multiple methods before accessing critical systems. By limiting access, SMBs can significantly minimize their risk exposure.Regular Audits and UpdatesAccess control policies must be regularly audited and updated to remain effective. As companies grow, adopt new technologies, or restructure their teams, access requirements may change, making it necessary to review who has access to sensitive information. Regular audits of user permissions ensure access is appropriately restricted and help uncover potential vulnerabilities. SMBs should also keep up with technological advancements and regulatory changes that may impact their security policies. For example, a company handling personal data may need to adjust its access policies to comply with new data protection laws, such as GDPR or CCPA.5. Enhancing Employee Security AwarenessTraining Programs for EmployeesSecurity awareness training is an essential part of any insider threat mitigation strategy. Employees are often the first line of defense against insider threats, and ensuring they understand security best practices can significantly reduce risks. SMBs should implement regular training programs to educate staff on identifying phishing emails, recognizing suspicious behavior, and protecting sensitive data. These training sessions should be mandatory and updated to reflect new threats or technologies. By instilling a strong sense of security and responsibility among employees, businesses can reduce accidental leaks and empower workers to report potential threats.Creating a Security-Conscious CultureBeyond training, SMBs must foster a security culture where employees feel a shared responsibility for protecting the organization's data. This can be achieved by encouraging open communication about security risks and promoting a non-punitive approach to reporting mistakes. When employees are comfortable reporting potential security issues or acknowledging errors without fear of retribution, the organization can address vulnerabilities faster. Leadership should lead by example, emphasizing the importance of security at all company levels. Secure password managers and data encryption software can help employees make better daily security decisions.6. SMB Insider Threat SolutionsCustomized Solutions for SMBsSMBs face unique challenges regarding insider threats, and several solutions are designed specifically for smaller businesses. These solutions often prioritize ease of use, scalability, and cost-effectiveness, ensuring that SMBs can implement them without needing a large IT team. Some options include cloud-based security platforms that offer real-time threat monitoring, employee behavior analysis, and integrated access control management. SMBs should evaluate these solutions based on their specific needs, ensuring that the chosen tools can seamlessly integrate into existing systems without disrupting business operations.Integration and ImplementationCareful planning and a clear understanding of the organization's security infrastructure are necessary to implement an insider threat solution. Small and medium-sized businesses (SMBs) should begin by thoroughly assessing their current systems and identifying gaps in their defenses. Once a solution has been chosen, it is essential to ensure that employees are effectively trained to use it. Integration should be carried out in phases, with continuous monitoring to measure the new system's effectiveness. Regular reviews and updates are necessary to adapt the solution to evolving threats and ensure ongoing protection.Summary of Key PointsInsider threats pose a significant risk to SMBs, especially those with limited resources dedicated to security. Businesses can significantly reduce the chances of a damaging insider attack by identifying potential hazards, implementing robust access control policies, and leveraging behavioral monitoring technologies. Additionally, enhancing employee security awareness and creating a culture can help prevent accidental leaks and deter malicious actors.As cybersecurity technology advances, small and medium-sized businesses (SMBs) must proactively address insider threats. In the future, managing insider threats will likely involve improvements in AI-powered detection systems and more customized solutions for smaller businesses. SMBs that stay vigilant, regularly update their security measures, and cultivate a security-conscious workforce will be better equipped to protect their assets and succeed in the digital age.If you need help with your security strategy, CPF Coaching is here for you.Visit https://www.cpf-coaching.com/booking to have an introductory conversation. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
10:1014/10/2024

Understanding and Mitigating Phishing Attacks in SMBs
Phishing attacks pose a growing threat to Small and Medium Businesses (SMBs), targeting their sensitive data and financial resources. These deceptive tactics, often delivered through fraudulent emails, trick employees into revealing confidential information or unknowingly downloading malware. For SMBs, the impact of a successful phishing attack can be devastating, leading to significant financial loss, data breaches, and reputational damage. In this guide, we'll explore the rising danger of phishing and the importance of solid email security. We'll also provide actionable strategies to protect your business from these increasingly sophisticated threats.SMB Tech & Cybersecurity Leadership Newsletter is a reader-supported publication. To receive new posts and support my work, consider becoming a free or paid subscriber.1. Introduction to Phishing Attacks in SMBsPhishing attacks have significantly threatened Small and Medium Businesses (SMBs). These attacks involve malicious actors sending deceptive emails to trick recipients into revealing sensitive information. The impact on SMBs can be severe, leading to financial loss, data breaches, and reputational damage. Recent statistics show a sharp rise in phishing attacks targeting SMBs, highlighting the need for robust security measures.Email security is crucial in protecting SMBs from phishing attacks. Without proper safeguards, businesses are vulnerable to various email security threats such as malware, ransomware, and spear-phishing. Ensuring robust email security helps prevent unauthorized access and protects sensitive information.This guide educates readers on phishing prevention, threat identification, and effective response strategies. By the end, you will have a comprehensive understanding of how to protect your SMB from phishing attacks.2. Phishing Prevention StrategiesImplementing robust email security measures is one of the first steps in phishing prevention. These include using email filters and spam detection tools to identify and block suspicious emails. Secure email gateways add another layer of protection by inspecting inbound and outbound emails for threats.It is crucial to train employees to recognize phishing attempts. Regular updates and simulated phishing exercises can help employees stay vigilant. Teaching them to look for red flags, such as suspicious links and unfamiliar senders, can significantly reduce the risk of falling for phishing scams.Crafting clear policies on email use and security is essential. These policies should outline acceptable email practices and procedures for reporting suspicious emails. Regular audits and compliance checks ensure guidelines are followed and updated.3. Identifying Phishing ThreatsUnderstanding common phishing tactics is critical to identifying threats. Phishing emails often contain urgent messages prompting immediate action, such as clicking a link or providing personal information. Differentiating between phishing and spear-phishing attacks, which are more targeted, is also essential.Utilizing AI and machine learning can enhance threat detection. These technologies analyze email patterns and flag suspicious activities. Integrating threat intelligence feeds into your security infrastructure provides real-time updates on emerging threats.Continuous monitoring is vital for identifying phishing threats promptly. Tools and software that offer 24/7 monitoring ensure that any suspicious activity is detected and addressed immediately. This proactive approach helps in mitigating potential damage.4. Developing Effective Response StrategiesOnce a phishing attempt is identified, immediate action is required. Isolating affected systems prevents the spread of malicious software. Following a predefined response plan is crucial to minimize damage and secure your network.Informing stakeholders and affected parties is critical in managing a phishing incident. Transparent communication helps maintain trust, and managing public relations effectively ensures that your business reputation remains intact.After addressing the immediate threat, reviewing and revising security measures is essential. Conducting a post-mortem analysis helps identify weaknesses and prevent future attacks. Implementing lessons learned ensures continuous improvement in your security posture.5. Attack Simulation and Continuous ImprovementRegular phishing attack simulations prepare your team for real threats. These simulations help identify vulnerabilities and improve response strategies. They also provide valuable insights into how employees react to phishing attempts.Continuous improvement is vital for maintaining strong security measures. Regular updates and enhancements based on simulation results ensure your defenses remain effective. Encouraging a culture of constant learning and adaptation keeps your team prepared for evolving threats.Collecting and analyzing user feedback is crucial for refining training and security protocols. This feedback helps identify areas for improvement and ensures that security measures are effective and current.ConclusionEmail security, phishing prevention strategies, threat identification, user training, and effective response strategies are essential. Each plays a crucial role in protecting SMBs from phishing attacks.Mitigating phishing attacks requires a proactive and comprehensive approach. SMBs must stay vigilant and continuously improve security measures to protect against evolving threats. By implementing the strategies outlined in this guide, SMBs can significantly reduce the risk of phishing attacks and safeguard their business.Phishing attacks pose a severe threat to SMBs, but with robust email security, user training, and effective response strategies, businesses can defend against these malicious threats. Continuous improvement and vigilance are vital to maintaining a secure environment. Stay informed, stay prepared, and keep your business safe.Product of the Week: INE TrainingINE offers a wide range of training programs to help your technical and development teams take the necessary actions to protect your organization. These teams can then serve as your first line of support in aiding your users with their awareness and security posture. Whether you are an individual or a company, INE provides training options that you can use today!Thanks for reading SMB Tech & Cybersecurity Leadership Newsletter! If you found value in this post, share it with others who might appreciate it as well. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
05:1827/09/2024

Enabling a SMB Security with Log Analysis and SIEM
The Business Value of Log Analysis and SIEM for SMBsAs threats become more sophisticated, robust security measures are paramount, even for small-medium businesses. One critical component of a comprehensive security strategy is log analysis and Security Information and Event Management (SIEM). These tools allow SMBs to detect potential threats early, allowing for timely intervention and mitigation. Log analysis involves reviewing and interpreting logs generated by computers, networks, and applications. These logs capture a wide range of activities, from user actions to system errors, providing invaluable insights into the health and security of IT environments. SIEM systems take this further by centralizing log data from multiple sources, correlating events, and providing real-time analysis to detect and respond to security incidents. For SMB leaders and security teams, investing in log analysis and SIEM can significantly enhance threat detection capabilities, improve compliance, and optimize operational efficiency.SMB Tech & Cybersecurity Leadership Newsletter is a reader-supported publication. To receive new posts and support my work, consider becoming a free or paid subscriber.Log analysis is the foundation of effective cybersecurity, providing invaluable insights into the activities occurring within an organization's IT infrastructure. Businesses can uncover patterns, anomalies, and potential security incidents that might go unnoticed by meticulously examining log files generated by various systems, applications, and network devices. SIEM systems take this further by aggregating and correlating data from multiple sources, offering a holistic view of an organization's security posture and enabling real-time threat detection and response.Tasks and Organizational ValueImplementing log analysis and SIEM can transform how SMBs manage their cybersecurity efforts. These solutions go beyond mere security enhancements; they contribute to operational efficiency, regulatory compliance, and overall business resilience.* Real-time Threat Detection: By continuously monitoring logs, SIEM systems can identify suspicious activities, such as unauthorized access attempts or unusual network traffic patterns. This allows businesses to respond quickly, minimizing potential damage from cyber threats.* Compliance and Reporting: Many industries have strict regulatory requirements for data security and privacy. Log analysis helps ensure compliance by providing detailed audit trails and reports that can be used to demonstrate adherence to regulations like GDPR or HIPAA.* Operational Efficiency: Log analysis tools automate the collection and parsing of log data, reducing the manual effort required by IT teams. This saves time and allows staff to focus on more strategic initiatives, improving overall productivity.Current Challenges and SolutionsDespite the clear benefits of implementing log analysis, SIEM systems, and partnering with MSSPs, SMBs often encounter significant challenges in adopting and optimizing these solutions. These obstacles range from resource constraints to the sheer complexity of modern cyber threats, creating a landscape that can be daunting for businesses with limited IT and security resources.* Resource Constraints: Limited budgets and personnel can make it difficult for SMBs to deploy and maintain sophisticated SIEM systems. To address this, businesses can explore open-source or cloud-based services that offer scalability and cost-effectiveness.* Data Overload: The sheer volume of log data can be overwhelming, leading to alert fatigue and potential oversight of critical incidents. Effective log management strategies, such as data filtering and prioritization, can help manage this influx and ensure that only relevant alerts are escalated.* Complexity of Integration: Integrating SIEM systems with existing IT infrastructure can be complex. Choosing solutions with user-friendly interfaces and robust support can ease this process, ensuring seamless integration and operation. Partnering with a Managed Security Service Provider could be another avenue to consider.Optimizing with Future SolutionsAs the cybersecurity landscape evolves, so must the strategies and tools used to protect digital assets. The future of log analysis, SIEM systems, and managed security services holds exciting possibilities for enhancing threat detection, streamlining operations, and improving overall security postures.* Leverage AI and Machine Learning: Incorporating AI and machine learning into log analysis can enhance threat detection by identifying patterns and anomalies that traditional methods might miss. These technologies can also automate responses, reducing the time to mitigate threats.* Adopt a Zero Trust Model: Implementing a Zero Trust security framework can complement log analysis efforts by ensuring all access requests are verified and monitored, regardless of origin. This approach enhances security by minimizing the risk of insider threats and lateral movement within networks.* Continuous Training and Education: The cybersecurity landscape constantly evolves, so ongoing training for security teams is crucial. Investing in education ensures that staff are equipped with the latest skills and knowledge to effectively utilize log analysis and SIEM tools.Using a Managed Security Service Provider (MSSP) over an in-house Security Operations Center (SOC) offers several cost benefits, particularly for small and medium-sized businesses (SMBs). Here are the primary cost advantages:Cost Benefits of Using an MSSP* Cost Efficiency: Cost efficiency is one of the most significant benefits of using an MSSP. Establishing an in-house SOC involves substantial expenses, including hiring skilled cybersecurity professionals, purchasing hardware and software, and maintaining facilities. MSSPs, on the other hand, spread these costs across multiple clients, allowing businesses to access high-quality security services at a fraction of the cost.* Scalability and Flexibility: MSSPs offer scalable solutions that can adjust to a business's changing needs without additional capital investment. This flexibility is particularly beneficial for SMBs that may experience fluctuating demands and cannot afford the financial burden of constantly upgrading their in-house SOC capabilities.* Access to Advanced Technologies: MSSPs provide access to cutting-edge security tools and technologies, such as Security Information and Event Management (SIEM) systems, without the direct costs associated with purchasing and maintaining these tools in-house. This access ensures businesses can leverage the latest security innovations without significant expenses.* 24/7 Monitoring and Support: MSSPs offer round-the-clock monitoring and support, which would require significant investment if managed internally. This continuous service ensures that businesses are protected at all times, including nights, weekends, and holidays, without hiring additional staff for these shifts.* Reduced Overhead and Operational Costs: By outsourcing to an MSSP, businesses can convert fixed costs into variable costs, allowing them to pay only for the needed services. This model reduces overhead and operational costs, freeing up resources that can be allocated to other strategic business initiatives.Partnering with an MSSP can provide SMBs with a cost-effective, scalable, and technologically advanced security solution. This allows them to focus on their core business activities while ensuring robust cybersecurity protection.Actionable SummaryA strategic approach is essential for SMB leaders looking to harness the power of log analysis, SIEM systems, and MSSPs to bolster their cybersecurity defenses. This section provides a roadmap for organizations seeking to implement or optimize these critical security measures, offering practical steps to enhance threat detection capabilities, ensure compliance, and improve overall security posture.* Evaluate and Choose the Right Tools: Assess your organization's needs and select log analysis and SIEM solutions that align with your budget and operational requirements.* Implement and Integrate: Ensure seamless integration of chosen tools with existing IT infrastructure, prioritizing solutions with user-friendly interfaces and firm support. Assess whether an MSSP could help optimize your monitoring posture.* Train and Educate: Train your security teams on the latest technologies and best practices in log analysis and threat detection.By focusing on these areas, SMBs can significantly improve their ability to detect and respond to cybersecurity threats, safeguard their operations, and ensure compliance with industry regulations.Thanks for reading SMB Tech & Cybersecurity Leadership Newsletter! If you have found value in this post, please share it with others and consider becoming a subscriber.Proudshout out: INEReady to learn with INE? Discover content across Networking, Cybersecurity, Cloud Computing, and Data Science for IT professionals at every level.Why INE? Affordable | Hands-On | Continuous This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
07:4302/09/2024

Enhancing Threat Detection in SMBs: A Guide to NIST CSF Detection Capabilities
Understanding the Importance of Threat Detection in SMBsSmall and medium-sized businesses are increasingly vulnerable to cyber threats. To effectively scale and innovate, they must insert cybersecurity mechanisms that secure their assets and data for their customers. In any robust cybersecurity strategy, threat detection certainly needs to be included. This goes above traditional monitoring by hunting for potential threats across all planes of business operations: data, control, and identity. It is in these broad areas that the leaders of SMBs can make a difference in the detection capabilities of the NIST Cybersecurity Framework and provide a more secure environment for their business.SMB Tech & Cybersecurity Leadership Newsletter is a reader-supported publication. To receive new posts and support my work, consider becoming a free or paid subscriber.The Role of Data, Control, and Identity PlanesIn cybersecurity, understanding the different planes of business operations—data, control, and identity—is crucial for effective threat detection. Each plane represents a unique aspect of your business's digital ecosystem that requires specific attention and strategies to safeguard against potential threats. By focusing on these planes, SMB leaders can develop a more comprehensive approach to threat detection that aligns with the NIST Cybersecurity Framework (CSF). This section will explore the significance of each plane and how they contribute to a robust cybersecurity posture.Data Plane: The data plane involves processing, storing, and transmitting data within a business. Effective threat detection ensures that sensitive information is safeguarded against unauthorized access and breaches. Here's where advanced data monitoring tools come in. These tools can help identify unusual patterns or anomalies that may indicate a cyber threat, giving you the reassurance that you're one step ahead in protecting your business.Control Plane: The control plane includes the systems and processes that manage data flow and access within the organization. Threat detection here focuses on ensuring that only authorized personnel have access to critical systems and data. By monitoring control plane activities, businesses can prevent unauthorized changes and detect potential insider threats, keeping you vigilant and aware of potential risks.Identity Plane: The identity plane pertains to the authentication and authorization of users accessing business systems. Effective threat detection in this plane involves monitoring user activities and ensuring robust access controls. Implementing multi-factor authentication and identity management solutions can significantly reduce the risk of identity-based attacks.Examples of Threat Detection Tasks and Their ValueImplementing threat detection capabilities involves various tasks that, when executed effectively, can significantly enhance an organization's security posture. From continuous monitoring to anomaly detection, these tasks are designed to identify and mitigate potential threats before they can cause harm. Understanding the value of these tasks helps build a resilient cybersecurity strategy and demonstrates the tangible benefits to stakeholders. This section will delve into specific threat detection tasks and highlight their importance to your organization.* Continuous Monitoring: By continuously monitoring network traffic and user activities, businesses can quickly identify and respond to potential threats. This proactive approach helps minimize the impact of cyber incidents and ensures business continuity.* Anomaly Detection: Machine learning algorithms can be utilized to detect anomalies in data and user behavior, providing early warnings of potential threats. This allows businesses to address vulnerabilities before attackers exploit them.* Incident Response Planning: Developing and regularly updating an incident response plan ensures businesses are prepared to handle cyber incidents effectively. This reduces downtime and mitigates the financial and reputational impact of breaches.Current Environmental Challenges and Overcoming ThemThe cybersecurity landscape constantly evolves, presenting SMBs with many challenges in implementing effective threat detection strategies. Limited resources, a shortage of skilled personnel, and the ever-changing nature of cyber threats are just a few hurdles businesses must overcome. However, with the right approach and tools, these challenges can be transformed into opportunities for strengthening security measures. This section will discuss the challenges SMBs face and provide insights into overcoming them to build a more secure business environment.SMBs face several challenges in implementing effective threat detection strategies, including limited resources, lack of expertise, and evolving threat landscapes. To overcome these challenges, businesses can:* Leverage Managed Security Services: Partnering with managed security service providers (MSSPs) can provide SMBs with access to advanced threat detection tools and expertise without significant in-house investment.* Invest in Employee Training: Regularly training employees on cybersecurity best practices can help prevent human errors that lead to security breaches.* Adopt Scalable Solutions: Implementing scalable cybersecurity solutions allows businesses to adapt to changing threats and needs without significant disruptions.Optimizing Threat Detection with Future SolutionsAs technology advances, so do the methods and tools available for threat detection. Embracing these innovations can provide SMBs with more efficient and effective ways to protect their digital assets. Future solutions offer promising avenues for optimizing threat detection capabilities, from artificial intelligence to zero trust architectures. In this section, we will explore potential future solutions that SMBs can leverage to enhance their cybersecurity strategies and stay ahead of emerging threats.Looking ahead, SMBs can optimize their threat detection capabilities by:* Embracing Artificial Intelligence (AI): AI-driven threat detection solutions can analyze vast amounts of data in real time, providing more accurate and timely threat identification.* Implementing Zero Trust Architecture: Adopting a zero-trust approach ensures that all users and devices are continuously verified, reducing the risk of unauthorized access.* Utilizing Threat Intelligence: Integrating threat intelligence feeds into security systems can provide businesses with up-to-date information on emerging threats, enabling proactive defense measures.Actionable SummaryTo enhance threat detection capabilities, SMB leaders should focus on the following action items:* Assess Current Security Posture: Conduct a thorough assessment of existing security measures and identify areas for improvement.* Invest in Technology and Training: Allocate resources to implement advanced threat detection tools and provide ongoing employee training.* Develop a Comprehensive Incident Response Plan: Ensure the business is prepared to respond swiftly and effectively to cyber incidents.By prioritizing threat detection across the data, control, and identity planes, SMBs can build a resilient cybersecurity posture that supports their growth and innovation goals.Product of the Week: YouAttestYouAttest has created a tool that is right for MSPs for identity compliance:• Plugs into existing identity systems in minutes• With NO API/coding experience, 100% GUI-driven• Can be integrated/supported with/ current MSP personnel• Anyone who can manage Azure AD, Okta, or similar IAM can manage YouAttestYouAttest is the fastest time-to-value identity audit product on the market.YouAttest identity audits specifically map to NIST SP 800-53 AC-1, AC-4, AC-6 and meet the following identity compliance requirements for the following markets:• Health Care: HIPAA/HITRUST• Financial: SOX, GLB• Retail: PCI-DSS• Cloud: SOC• D.o.D. Contractors: CMMC• Int’l: ISO 27001, GDPRIf you would like to learn more about how YouAttest or if I can help you with your identity governance, reach out to me. YouAttest: [email protected] (Let them know CPF Coaching sent you their way)https://youattest.com/youattest-in-the-news/Thanks for reading SMB Tech & Cybersecurity Leadership Newsletter! If this episode has provided you with value and you know others who could use this, please do share with them. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
07:2226/08/2024

Enhancing Security in Open-Source Code for SMBs
In the digital world today, it is more often than not that small and medium-sized businesses are found turning to open-source code and public software repositories to be able to build and enhance their technological capabilities. On one hand, such resources bring about considerable cost savings and advantages of innovation, but on the other hand, they also bear the potential security risks that might compromise the integrity of business operations. It is against this backdrop that, as a senior cybersecurity leader and advisor, I come forth to place emphasis on the security and integrity of open-source code and how SMB leaders and security teams can effectively deal with these risks.SMB Tech & Cybersecurity Leadership Newsletter is a reader-supported publication. To receive new posts and support my work, consider becoming a free or paid subscriber.Open-source software has become a cornerstone for many businesses, providing a flexible and cost-effective way to access cutting-edge technology. However, the very nature of open-source code—its openness and collaborative development—can also make it a target for malicious actors seeking to exploit vulnerabilities. For SMBs, which may lack the extensive resources of larger enterprises, the challenge is to harness the benefits of open-source software while mitigating the associated risks. By prioritizing security and integrity in open-source code, SMBs can protect their assets, maintain customer trust, and ensure business continuity.Examples of Use Cases and their value* Code Review and Vulnerability Assessment: It is crucial to regularly review open-source code for vulnerabilities. This task helps identify potential security flaws before they can be exploited, thereby protecting the organization from breaches and data loss.* Implementing Security Tools: Tools such as static code analyzers and dependency checkers can automate the process of detecting vulnerabilities in open-source components. This not only saves time but also enhances the organization's overall security posture.* Community Engagement and Contribution: Participating in open-source communities lets businesses stay informed about the latest security patches and updates. Contributing to these communities can foster goodwill and collaboration, leading to more robust and secure software solutions.Current Environmental Challenges and SolutionsThe open-source ecosystem is vast and constantly evolving, which presents several challenges:* Rapidly Changing Codebases: Maintaining frequent updates and patches can be daunting. SMBs can overcome this by implementing automated update management systems that ensure the timely application of security patches.* Lack of In-House Expertise: Many SMBs struggle with limited cybersecurity expertise. Partnering with external cybersecurity firms or consultants can provide support and guidance to manage open-source risks effectively.* Supply Chain Vulnerabilities: Software dependencies' interconnected nature can introduce vulnerabilities. Conducting thorough supply chain risk assessments and utilizing tools that map and monitor dependencies can help mitigate these risks.Potential Future SolutionsLooking ahead, SMBs can optimize their approach to open-source security by:* Adopting AI and Machine Learning: These technologies can enhance threat detection and response capabilities, providing real-time insights into potential vulnerabilities and threats.* One possible use case includes the ability to analyze SBOMs, connect software packages to those in use in the environment, and aid with the remediation of patching or updates.* Developing a Security-First Culture: Encouraging a mindset where security is integrated into every aspect of software development and deployment can lead to more secure outcomes. This involves training employees and fostering an environment where security is everyone's responsibility.Actionable SummaryTo effectively manage the security and integrity of open-source code, SMB leaders and security teams should focus on the following action items:* Conduct regular code reviews and vulnerability assessments.* Implement automated tools for detecting and managing vulnerabilities.* Engage with open-source communities for the latest security updates.* Partner with cybersecurity experts to enhance in-house capabilities.* Foster a security-first culture within the organization.By taking these steps, SMBs can leverage the benefits of open-source software while minimizing security risks, ultimately enhancing their resilience in an increasingly digital world.Thanks for reading SMB Tech & Cybersecurity Leadership Newsletter! If you found value from this post, sharing it with others would mean the world to us.Product shout-out: LearnWorldsAt CPF Coaching, we're always on the lookout for top-notch tools that empower our clients to the max. This is why we couldn't, but we are very excited about recommending LearnWorlds. Just recently named "Top User-rated Online Course Platform & LMS," LearnWorlds is a supreme platform that allows the world to leverage your knowledge and talents. Whether you're an educator, coach, or business leader, it really has everything you need to run highly engaging and impactful online courses. Time to make a difference—find a way to share your value with those who need it the most! This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
05:3519/08/2024

The Business Value of PKI Encryption for SMBs: Enhancing Security and Compliance
With a digital and cloud-first approach used by Small and medium-sized businesses (SMBs), they face ever-increasing cybersecurity threats. As a cybersecurity leader, it is crucial to implement robust security measures that protect your organization and align with industry standards like the NIST Cybersecurity Framework (CSF). One such measure is Public Key Infrastructure (PKI) encryption. PKI is a framework that uses cryptographic keys to secure communications, authenticate users, and ensure data integrity. This blog post will delve into PKI encryption's purpose and business value, how it can help identify and detect potential threats, and how these steps align with the NIST CSF framework.Cybersecurity Leadership & SMB Security Development is a reader-supported publication. To receive new posts and support my work, consider becoming a free or paid subscriber.How PKI Encryption Can Help SMBs Detect Threats and Align with NIST CSFAs we navigate the complexities of cybersecurity, it's essential to understand that PKI is not just a technical solution but a strategic asset that can significantly enhance your business's security posture and operational efficiency.Using PKI Encryption in SMBsIn an era where data breaches and cyber attacks are becoming increasingly common, PKI encryption is a powerful tool in the SMB's cybersecurity arsenal. By implementing PKI, businesses can create a secure environment protecting sensitive information and fostering stakeholder trust and confidence. Let's explore the key benefits that make PKI encryption invaluable for SMBs.Enhancing Security and Trust: PKI encryption provides a high level of security by encrypting data and ensuring that only authorized parties can access it. This is particularly important for SMBs that handle sensitive customer information, financial data, or intellectual property. By implementing PKI, businesses can build trust with their clients and partners, knowing their data is protected against unauthorized access.Authentication and Access Control: PKI enables robust authentication mechanisms, such as digital certificates, which verify the identity of users and devices. This helps prevent unauthorized access to critical systems and data. For SMBs, this means a reduced risk of data breaches and insider threats, leading to a more secure business environment.Compliance and Regulatory Requirements: Many industries have stringent compliance requirements regarding data security and privacy. PKI helps SMBs meet these requirements by providing a robust framework for securing communications and data. This ensures compliance and reduces the risk of legal and financial penalties associated with data breaches.PKI Tasks in your Day-to-Day and Their ValueUnderstanding the practical applications of PKI is crucial for SMB leaders to appreciate its value entirely. PKI isn't just a theoretical concept; it has tangible, real-world applications that can significantly improve your business's security and operational efficiency. Let's examine some critical PKI tasks and how they translate into concrete benefits for your organization.Digital Signatures: Implementing digital signatures for documents and transactions ensures data integrity and non-repudiation. This means that any changes to the document can be detected, and the sender cannot deny having sent the document. For SMBs, this is invaluable in maintaining the authenticity of contracts, invoices, and other critical business documents.Secure Email Communication: PKI can encrypt email communications, ensuring that sensitive information is only accessible to the intended recipient. This is particularly important for SMBs that frequently communicate confidential information with clients and partners.SSL/TLS Certificates: Using SSL/TLS certificates to secure websites and online services helps protect against man-in-the-middle attacks and ensures that data transmitted between the user and the server is encrypted. This protects customer data and enhances the business's reputation by providing a secure online experience.Current Environmental Challenges for SMBs and Some Potential SolutionsWhile the benefits of PKI are clear, implementing and maintaining this infrastructure is not without its challenges. Many SMBs face hurdles that can seem daunting at first glance. However, with the right approach and understanding, these obstacles can be overcome, allowing businesses to reap the full benefits of PKI. Let's explore some of the common challenges and their solutions.Complexity and Cost: One of the main challenges SMBs face when implementing PKI is its perceived complexity and cost. To overcome this, businesses can leverage managed PKI services that offer scalable solutions without the need for extensive in-house expertise. These services provide the necessary infrastructure and support, making PKI implementation more accessible and cost-effective.Integration with Existing Systems: Integrating PKI with existing IT systems and applications can be challenging. SMBs can address this by working with vendors that offer seamless integration options and provide comprehensive documentation and support. Additionally, thorough planning and testing before full-scale implementation can help identify and resolve potential issues.Ongoing Management and Maintenance: Maintaining a PKI infrastructure requires ongoing management, including certificate renewal, revocation, and monitoring. SMBs can streamline this process by using automated tools and services that handle these tasks, reducing the administrative burden on IT teams.Future Optimization PossibilitiesAs technology continues to evolve rapidly, so too does the potential for PKI optimization. The future of PKI holds exciting possibilities for SMBs, with emerging technologies and innovative approaches promising to make PKI even more powerful and accessible. By staying ahead of these trends, businesses can position themselves to leverage PKI in increasingly sophisticated ways. Let's explore some future optimization possibilities that SMBs should keep on their radar.Automated Certificate Management: As PKI adoption grows, automated certificate management solutions are becoming more prevalent. These tools can automatically issue, renew, and revoke certificates, reducing the risk of human error and ensuring continuous security.Integration with Emerging Technologies: PKI can be integrated with emerging technologies such as the Internet of Things (IoT) and blockchain to enhance security. For example, PKI can provide secure communication and authentication for IoT devices, ensuring that only authorized devices can access the network.Advanced Threat Detection: By integrating PKI with advanced threat detection and response systems, SMBs can enhance their ability to detect and respond to potential threats. This includes using PKI to secure communication channels and authenticate users in real-time, providing an additional layer of security.Advanced threat detection is crucial for SMBs to stay ahead of potential attacks, by integrating Public Key Infrastructure (PKI) with advanced threat detection and response systems. This integration creates a powerful synergy that not only secures communications but also provides real-time threat intelligence and response capabilities.
Secure Communication Channels: PKI forms the backbone of secure communication within an organization's network. When integrated with threat detection systems, it ensures that all data exchanged between systems, devices, and users is encrypted and authenticated. This means that even if a threat actor manages to intercept communications, they won't be able to decipher the content. Moreover, any attempt to tamper with the data will be immediately detected, triggering an alert in the threat detection system.
For example, if an attacker tries to inject malicious code into an encrypted communication channel, the PKI system will detect the breach of integrity, and the threat detection system can immediately isolate the affected systems to prevent further spread.
Real-Time User Authentication: PKI provides strong authentication mechanisms through digital certificates. When combined with advanced threat detection, this allows for continuous, real-time verification of user identities. Any anomalies in user behavior or attempts to use compromised credentials can be instantly flagged and investigated.
Consider a scenario where an employee's credentials are stolen. Even if the attacker uses the correct username and password, the PKI-based authentication can detect that the login attempt is coming from an unfamiliar location or device. The threat detection system can then trigger additional authentication steps or block the access attempt altogether, preventing a potential data breach.
Automated Certificate Management and Monitoring: Advanced threat detection systems can monitor the status of digital certificates issued by the PKI. This automated monitoring can alert security teams to expired or revoked certificates, preventing potential vulnerabilities that could be exploited by attackers.
For instance, if a certificate is about to expire, the system can automatically initiate the renewal process. If a certificate is suddenly revoked, it can trigger an investigation to determine if this is due to a security breach or a routine administrative action.
Enhanced Visibility and Threat Intelligence: By integrating PKI with threat detection systems, SMBs gain enhanced visibility into their network activities. Every authenticated action, encrypted communication, and digital signature can be logged and analyzed. This wealth of data can be used to build comprehensive threat intelligence, helping to identify patterns of suspicious behavior or potential vulnerabilities.
For example, the system might detect an unusual pattern of certificate requests from a particular department, which could indicate a compromised system attempting to establish rogue secure connections.
Rapid Incident Response: In the event of a detected threat, the integration of PKI with advanced threat detection systems allows for rapid and precise response. The system can quickly revoke compromised certificates, isolate affected systems, and re-establish secure communications through new certificate issuance.
Imagine a scenario where a malware infection is detected on a company device. The threat detection system can immediately revoke the device's certificates, preventing it from accessing sensitive resources. Simultaneously, it can issue new certificates to clean devices, ensuring business continuity while the threat is contained and investigated.
By leveraging PKI in conjunction with advanced threat detection and response systems, SMBs can create a robust, multi-layered security environment. This integration not only secures communications and authenticates users but also provides the real-time intelligence and response capabilities necessary to combat today's sophisticated cyber threats. For SMBs looking to enhance their cybersecurity posture, this approach offers a powerful way to align with the NIST CSF framework, particularly in the areas of Identifying, Protecting, Detecting, and Responding.Actionable SummaryAs explored throughout this post, PKI encryption offers significant benefits for SMBs, from enhanced security to improved compliance and threat detection. However, understanding these benefits is just the first step. To truly leverage the power of PKI and align with the NIST CSF framework, SMB leaders and security teams need to take concrete actions. Here's a summary of key steps you can take to implement and optimize PKI in your organization.To leverage the full potential of PKI encryption and align with the NIST CSF framework, SMB leaders and security teams should:* Implement Digital Certificates: Use digital certificates for authentication, secure email communication, and SSL/TLS for websites.* Leverage Managed PKI Services: Consider using managed PKI services to reduce complexity and cost.* Automate Certificate Management: Utilize automated tools to manage the lifecycle of digital certificates, ensuring continuous security.By focusing on these critical areas, SMBs can enhance their security posture, build trust with clients and partners, and align with the NIST CSF framework.For more information on PKI encryption and its benefits, visit https://cpf-coaching.com/Thanks for checking out the SMB Tech & Cybersecurity Leadership Newsletter! If you found this post valuable, please consider sharing it with others who would appreciate it.Product of the Week: ClymAs business owners, it is vital to grasp and uphold data privacy in the modern interconnected business world. Ensuring data privacy is not just a trend; it is an essential responsibility. This means effectively managing your customers' personal information and understanding its acquisition, storage, and usage. By recognizing and respecting this right, you can establish transparent practices for handling customer data.It helps tailor your website’s privacy and accessibility requirements. I used it on my own website, and it was as simple as adding a small header/footer script to your page, into your Google Tag Manager, or a plugin for most website hosting providers. Check out getting Clym for your business’ website today. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
12:1705/08/2024

Empowering Small and Medium-Sized Businesses to Detect and Prevent Cyber Threats
Discover how Encryption & SSL can strengthen your SMB's cybersecurity posture, align with NIST CSF, and protect against emerging threats. Learn actionable steps to implement these vital security measures.Cybersecurity Leadership & SMB Security Development is a reader-supported publication. To receive new posts and support my work, consider becoming a free or paid subscriber.Encryption & SSL: Cornerstones of SMB Cybersecurity and NIST CSF AlignmentIn today's digital landscape, small and medium-sized businesses (SMBs) face an ever-growing array of cyber threats. As a seasoned cybersecurity advisor, I've witnessed firsthand the devastating impact of data breaches and cyber attacks on businesses that were caught unprepared. That's why I'm passionate about empowering SMB leaders and their security teams with the knowledge and tools they need to protect their digital assets effectively.One of the most crucial aspects of a robust cybersecurity strategy is the implementation of strong encryption and Secure Sockets Layer (SSL) protocols. These technologies safeguard your sensitive data and play a pivotal role in aligning your security practices with the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF). In this post, we'll explore the business value of focusing on encryption and SSL and how these measures can significantly enhance your ability to identify and detect potential threats.The Business Value of Encryption and SSL for SMBsEncryption and SSL are not just technical jargon; they're powerful tools that provide tangible benefits to your business. By implementing these security measures, you're taking proactive steps to protect your company's most valuable assets: its data and reputation.Encryption ensures that your sensitive information remains confidential, even if it falls into the wrong hands. This is particularly crucial for SMBs that handle customer data, financial information, or proprietary business strategies. On the other hand, SSL creates a secure data transmission channel, protecting information as it travels across networks. Together, these technologies form a formidable defense against data breaches and unauthorized access.Aligning with NIST CSF: Identify and DetectThe NIST Cybersecurity Framework provides a comprehensive approach to managing and reducing cybersecurity risk. Two critical functions within this framework are "Identify" and "Detect," which are significantly enhanced by properly implementing encryption and SSL.In the "Identify" function, encryption and SSL help you catalog and understand the data assets that need protection. Implementing these technologies requires you to take stock of sensitive information and prioritize its security. This process aligns perfectly with the emphasis of NIST CSF's asset management and risk assessment.For the "Detect" function, SSL certificates and encryption protocols can serve as early warning systems. Unusual encryption activities or attempts to bypass SSL can indicate potential threats, allowing your security team to detect and respond to incidents quickly.Practical Implementation and ChallengesImplementing encryption and SSL across your organization may seem daunting, but it's necessary in today's threat landscape. Start by identifying your most sensitive data and prioritizing its encryption. This could include customer information, financial records, and intellectual property.For SSL, ensure that all your public-facing websites and applications use HTTPS. This protects data in transit and boosts your search engine rankings and customer trust.One common challenge SMBs face is the misconception that robust encryption is too complex or expensive to implement. However, with the proper guidance and tools, even small businesses can achieve high security. Cloud-based solutions and managed security services have made enterprise-grade encryption more accessible.Another hurdle is keeping up with evolving encryption standards and SSL certificate management. Regular audits and updates are crucial to maintain the effectiveness of your security measures. Consider automating certificate renewals and implementing a centralized management system to streamline this process.Future-Proofing Your Encryption StrategyAs we look to the future, the importance of encryption and SSL will only grow. Quantum computing poses both a threat and an opportunity in encryption. While it can potentially break current encryption methods, it also paves the way for quantum-resistant algorithms.To stay ahead of the curve, SMBs should monitor post-quantum cryptography developments. The National Institute of Standards and Technology (NIST) is already working on standardizing quantum-resistant cryptographic algorithms. Familiarizing yourself with these emerging standards can help you prepare for the future of data protection.Additionally, consider exploring homomorphic encryption, which allows computations on encrypted data without decrypting it first. This technology could revolutionize handling sensitive data, especially in cloud environments.Actionable Summary: Strengthening Your SMB's Cybersecurity Posture* Conduct a thorough data inventory to identify sensitive information that requires encryption.* Implement SSL certificates on all public-facing websites and applications.* Develop an encryption key management strategy to ensure the security and availability of your encryption keys.To deepen your understanding of encryption and SSL in the context of SMB cybersecurity:* Enroll in online courses focused on cryptography and network security.* Attend cybersecurity conferences and workshops tailored for SMBs.* Engage with cybersecurity communities and forums to stay updated on best practices and emerging threats.Remember, cybersecurity is an ongoing journey, not a destination. By focusing on encryption and SSL, you're taking significant steps toward a more secure and resilient business. Stay vigilant, keep learning, and don't hesitate to seek expert advice when needed.Thank you for reading Cybersecurity Leadership & SMB Security Development. Share this post with SMB and tech leaders who might find it helpful and want to develop their cybersecurity programs.Product of the Week: SaneBoxAre you tired of sorting through junk in your inbox just to find the emails you really need? SaneBox does the sorting for you, saving the average user more than two hours a week on email management. Using its proprietary AI, SaneBox organizes your incoming emails into appropriate folders, so you’ll only see the important emails when you open your inbox. You don’t have to lift a finger, and there is nothing to install, either.With glowing reviews from TechCrunch, Forbes, The New York Times, and emailers everywhere, you can rest assured that you will fall in love with email again. TLDR: SaneBox is an AI-driven email management tool that saves the average user 2.5 hours per week by seamlessly organizing and filtering emails. Other SaneBox FeaturesIn addition to our acclaimed email management software, SaneBox offers additional features that help you spend more time outside the inbox. Some fan-favorite features include:* SaneLater - moves all unimportant emails into a separate folder (this is our bread and butter feature) * 🕳 SaneBlackHole: Banish unwelcome email senders and never hear from them again.* 🔔 SaneReminders: We’ll send a reminder to follow up when an email goes unanswered for 5 days.* ⏰ Snooze Folders: Hit “snooze” on an email, and it’ll pop back into your inbox when you’re ready for it.Additional features people love too:* 🌙 DoNotDisturb: Vacation? Focus time? Turn off emails so you don’t receive them until you want them.* 📥 Email Deep: Clean and Clear out unnecessary emails in bulk to declutter and save storage space.* 📎 SaneAttachments: Connect your email to your cloud services to safely store attachments.* 📄 SaneDigest: Get a daily digest of your emails to understand what’s going where and better train SaneBox. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
05:1129/07/2024

Lessons from Crowdstrike/Windows Cyber Outage: Key Takeaways for Robust Cybersecurity
Discover essential takeaways from yesterday’s cyber outage, including understanding digital supply chain risks, implementing robust change management, and developing a comprehensive incident response plan. Enhance your cybersecurity resilience today.Cybersecurity Leadership & SMB Security Development is a reader-supported publication. To receive new posts and support my work, consider becoming a free or paid subscriber.Lessons from Yesterday’s Cyber Outage: Key Takeaways for Robust CybersecurityCyber (or IT) outages can have devastating impacts on businesses, causing not only financial losses but also reputational damage. Yesterday's cyber outage was a stark reminder of the vulnerabilities that lurk within our interconnected systems. As organizations rely increasingly on digital technologies, understanding and mitigating these risks becomes paramount. Reflecting on the recent incident, several critical lessons have emerged that can help organizations fortify their defenses and enhance their incident response strategies. These takeaways highlight the importance of a comprehensive approach to cybersecurity, emphasizing the need for thorough risk assessment, robust change management, and an inclusive incident response plan. 1. Understand the Risks in Your Digital Supply ChainOne of the most crucial aspects of maintaining a secure digital environment is understanding the risks inherent in your digital supply chain or software development life cycle (SDLC). The cyber outage underscored the importance of thoroughly testing changes before large-scale deployments into production. This proactive approach identifies and mitigates potential vulnerabilities early, preventing disruptions and security breaches.* Risk Assessment: Regularly conduct risk assessments to identify and evaluate potential threats within your digital supply chain and SDLC. This includes understanding third-party dependencies and their associated risks.* Testing and Validation: Implement rigorous testing protocols, including penetration testing and vulnerability assessments, to validate changes before deployment. This helps in detecting flaws that cyber attackers could exploit.* Continuous Monitoring: Establish constant monitoring systems to monitor changes and their environmental impacts. This enables real-time detection of anomalies and swift action to mitigate risks.2. Implement a Robust Change Management ProcessA robust change management process is essential for handling unforeseen issues during deployments. The recent outage demonstrated the importance of being prepared to roll back changes that do not go as expected and responding effectively to minimize disruption.* Change Control: Develop a structured change control process that includes detailed documentation, approval workflows, and rollback procedures. This ensures that all changes are tracked and can be reversed if necessary.* Rollback Plans: Prepare rollback plans for every deployment. These plans should be tested regularly to ensure smooth execution in case of an unexpected issue.* Responsive Actions: Train your team to respond quickly and efficiently to unforeseen changes. This includes having a clear communication plan to inform stakeholders about the status and impact of the change.3. Develop a Comprehensive Incident Response PlanHaving an incident response plan that encompasses the entire business is vital. Cyber incidents can affect various aspects of operations, IT, cybersecurity, development, and other business functions. An inclusive incident response plan ensures that everyone knows their role and can contribute to a coordinated response.* Holistic Planning: Create an incident response plan that involves all business functions. Ensure that all team members clearly define and understand roles and responsibilities.* Decision Trees: Develop decision trees to guide actions during different incidents. This helps make informed decisions quickly, even when the nature of the incident is unclear.* Regular Drills: Conduct incident response drills to ensure all team members are prepared to act swiftly and effectively. These drills should simulate malicious and non-malicious incidents to cover all potential scenarios.Thank you for reading Cybersecurity Leadership & SMB Security Development. If you love the content of this post, we would love it if you shared it with others.ConclusionYesterday’s cyber outage powerfully reminds us of the importance of robust cybersecurity practices. By understanding and mitigating risks in your digital supply chain, implementing a solid change management process, and developing a comprehensive incident response plan, organizations can significantly enhance their resilience against cyber threats. Proactive preparation and continuous improvement are vital in maintaining a secure and reliable digital environment.Product of the Week: Nessus from TenableSecure Cloud Infrastructure Before Deployment The reliance on the cloud and infrastructure as code (IaC) to streamline development lifecycles has become crucial to every organization’s business. Yet, developers aren’t following security best practices before pushing to production, which increases risk. If unknown vulnerabilities are moved into production, taking the environment down will disrupt business continuity or force the organization to take on more risk. •Scans IaC repositories to programmatically detect cloud infrastructure misconfigurations and vulnerabilities in the software development lifecycle's design and build phases. •Leverages 500 prebuilt policies for IaC scanning •Prevents misconfigurations and vulnerabilities from reaching cloud instances •Provides a proactive approach to vulnerability assessment for cloud workloads •Scan for disruptive and costly vulnerabilities before code is deployed. •Prevent the downtime and additional costs and resources associated with remediating code after deploymentThank you for reading Cybersecurity Leadership & SMB Security Development. If you love the content of this post, we would love it if you shared it with others. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
06:0620/07/2024

Enhancing SMB Security: The Critical Role of Desktop Protection
In today's digital age, small and medium-sized businesses (SMBs) face increasing threats from cyber attacks, which can compromise sensitive data and disrupt operations. Desktop security, often overlooked, plays a crucial role in defending against these threats. For SMB leaders, focusing on desktop security not only helps in identifying and detecting potential threats but also aligns with the NIST Cybersecurity Framework (CSF) to enhance overall security posture.Cybersecurity Leadership & SMB Security Development is a reader-supported publication. To receive new posts and support my work, consider becoming a free or paid subscriber.Desktop security involves protecting endpoint devices such as computers, laptops, and workstations from cyber threats. Given that these devices are gateways to the organization's network, ensuring their security is paramount. By integrating desktop security measures with the NIST CSF, SMBs can create a robust defense mechanism that supports their business objectives and regulatory compliance requirements.Tasks and Their Business ValueImplementing desktop security involves several critical tasks that offer substantial value to the organization.* Endpoint Protection Solutions: Deploying antivirus and anti-malware software is the first line of defense against cyber threats. These solutions help detect and eliminate malicious software, protecting sensitive business data and maintaining operational continuity.* Patch Management: Regularly updating software and operating systems on desktops ensures that known vulnerabilities are patched. This reduces the risk of exploitation by cybercriminals and minimizes potential security breaches.* Access Control: Implementing strict access controls, such as multi-factor authentication (MFA) and role-based access, ensures that only authorized personnel can access critical systems and data. This helps prevent unauthorized access and potential data breaches.These tasks align with the NIST CSF’s core functions: Identify, Protect, Detect, Respond, and Recover. By addressing these areas, SMBs can systematically enhance their security posture, making it harder for attackers to compromise their systems.Current Environmental ChallengesSMBs often face unique challenges in implementing effective desktop security. Limited budgets and resources can make it difficult to invest in advanced security solutions. Additionally, the lack of dedicated IT security staff means that many SMBs do not have the expertise needed to manage and respond to security threats effectively.To overcome these challenges, SMBs can leverage cost-effective solutions such as cloud-based security services, which offer robust protection without the need for significant upfront investment. Training employees on basic cybersecurity practices can also enhance the overall security posture by reducing the likelihood of human error leading to security incidents.Optimizing Desktop Security with Future SolutionsLooking ahead, SMBs can optimize desktop security by adopting innovative technologies and practices.* Behavioral Analytics: Implementing tools that use machine learning to analyze user behavior can help detect anomalies and potential threats in real-time, providing an additional layer of security.* Zero Trust Architecture: Moving towards a zero trust model, where every access request is authenticated, authorized, and encrypted, ensures that even if a device is compromised, the risk of further exploitation is minimized.* Automation: Using automated tools for patch management, threat detection, and response can significantly reduce the burden on IT staff and ensure that security measures are consistently applied.By staying abreast of these advancements, SMBs can continuously improve their desktop security measures, aligning them with the evolving threat landscape and maintaining compliance with the NIST CSF.SummaryIn conclusion, focusing on desktop security is vital for SMB leaders to protect their organizations from potential cyber threats. By implementing endpoint protection solutions, managing patches effectively, and enforcing strict access controls, SMBs can align their security efforts with the NIST CSF. Overcoming challenges such as limited resources and expertise can be achieved through cost-effective solutions and employee training. Looking to the future, adopting behavioral analytics, zero trust architecture, and automation will help optimize desktop security, ensuring a robust defense against evolving cyber threats.Action Items:* Assess current desktop security measures and identify gaps.* Implement endpoint protection solutions and ensure regular patch management.* Enforce strict access controls and consider adopting MFA.* Train employees on basic cybersecurity practices.* Explore and adopt advanced security technologies like behavioral analytics and zero-trust architecture.Thank you for reading Cybersecurity Leadership & SMB Security Development . If you enjoyed this post, please share it with SMB and tech leaders.Product shout out of the week: SaneBoxKeeping a clean inbox is one of my most important productivity hacks.It makes everything easier. Nowadays, we get so much junk in our emails. And it's a waste of time going through it.But I've found a solution to steer clear of inbox overload.SaneBox is the all-in-one solution to email overload, called a "lifesaver" by PCMag, saving you at least 3 hours per week.Their trainable AI assistant identifies important emails and automatically organizes the rest to help you stay focused.Sign up today and save $25 on any subscription. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
04:1912/07/2024

Maximize Business Security: The Critical Purpose and Value of DDoS Protection
Learn how DDoS protection can safeguard your business by aligning with the Identify and Protect stages of the NIST Cybersecurity Framework. Discover practical strategies and future solutions for SMBs. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
08:3428/06/2024

The Framework Foundation of NIST CSF as Risk Management for CISO & Practitioners
Understanding and Implementing the NIST Cybersecurity Framework (CSF): A Guide for CISOs and PractitionersIn this episode of the Cyber Hub podcast, James Azar and Chris Filone discuss the practical application of the NIST Cybersecurity Framework (CSF) for organizational risk management. They delve into the framework's components, such as Identify, Protect, Detect, Respond, and Recover, and provide insights on how these can be tailored to suit the specific needs of any organization. The discussion emphasizes the importance of integrating privacy considerations and continuously monitoring and updating security measures to adapt to evolving threats and regulatory requirements.Actionable Takeaways:* Understand the NIST CSF Structure: Familiarize yourself with the framework’s components and their application.* Perform a Gap Analysis: Identify gaps in your organization’s cybersecurity posture using the NIST CSF.* Implement Relevant Controls: Select and apply controls that align with your organization’s risk profile.* Integrate Privacy Considerations: Ensure privacy requirements are part of your cybersecurity strategy.* Continuous Monitoring and Improvement: Establish ongoing monitoring processes and regularly update security measures.Referenced links:The NIST Cybersecurity Framework (CSF) 2.0 (This is for the publication and links to many other resources)Cybersecurity Framework (CSF) - NIST CSWP 29 (This is the NICSF CSF Framework webpage) Navigating NIST's CSF 2.0 Quick Start Guides (Business and Community profile recommendations available here)NIST Cybersecurity Framework (CSF) 2.0 Reference Tool (Exportable in Excel and JSON) This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
32:5224/05/2024

Friday Conversation: Cybersecurity Frameworks Explained CIS, NIST, MITRE & More
Join James Azar and Chris Foulon on Friday Conversations podcast to unravel the complexities of cybersecurity frameworks like CIS, NIST, and MITRE. Learn their differences, practical applications, and how they impact cybersecurity strategies. Tune in for expert insights and actionable advice. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
28:3523/05/2024

Enhancing Business Security Through Identity Management in the NIST Cybersecurity Framework
Harnessing the Identify and Protect Stages of NIST CSF for Enhanced Threat ProtectionExplore how identity management is pivotal in the Identify and Protect stages of the NIST Cybersecurity Framework (CSF), offering robust defenses against evolving cyber threats.In today's digital-first environment, managing internal identities efficiently and securely is paramount for organizations across all industries. Identity management encompasses the methodologies and systems that allow businesses to authenticate and authorize individuals or groups to access resources within corporate environments. However, this process comes with complex challenges that can impact security, compliance, and operational efficiency. Understanding these challenges and employing strategic improvements is crucial for maintaining robust security protocols and safeguarding sensitive information. This introduction delves into organizations' everyday challenges in managing internal identities and provides practical tips for enhancing these processes. Additionally, it highlights the critical role of collaboration among various business units, such as Human Resources, IT, Compliance, and departmental management, in fostering a secure and compliant identity management framework.Introduction to Identity Management and the NIST Cybersecurity FrameworkIdentity management is critical to any organization’s cybersecurity strategy, particularly within the Identify and Protect stages of the National Institute of Standards and Technology’s Cybersecurity Framework (NIST CSF). This framework provides guidelines on preventing, detecting, and responding to cyber threats, with identity management as a cornerstone for safeguarding digital assets. It involves processes and technologies that help manage and secure identity information to ensure the right individuals access the appropriate resources at the right times for the right reasons.The Value and Impact of Identity Management TasksEffective identity management encompasses various tasks, each contributing uniquely to the organization's security posture. Key tasks include creating and managing user credentials, implementing multi-factor authentication (MFA), and continuously monitoring and updating access controls. These measures help reduce the risk of unauthorized access and potential breaches. For example, MFA adds layer of security that significantly mitigates the risk of compromised passwords.Challenges and Solutions in the Current EnvironmentToday’s businesses face numerous challenges in identity management, including managing access across varied IT environments and the growing sophistication of cyber threats. Organizations are increasingly turning to cloud-based identity and access management solutions that offer scalability, real-time access updates, and integrated security features to address these issues. Additionally, adopting artificial intelligence and machine learning for behavioral analysis can predict and prevent unauthorized access based on usage patterns.Looking Forward: Innovations and Strategies in Identity ManagementLooking ahead, the future of identity management is geared towards more integrated and predictive systems. Innovations such as blockchain for secure, decentralized management of digital identities and biometric authentication methods are on the rise. These technologies not only enhance security but also improve user experience by streamlining authentication processes.Actionable SummaryTo fully leverage identity management within the Identify and Protect stages of the NIST CSF, organizations should:* Evaluate and update their identity management policies regularly.* Invest in training for IT staff and users to recognize phishing attempts and other common cyber threats.* Consider adopting emerging technologies like blockchain and advanced biometrics to stay ahead of potential security threats.For further learning and detailed understanding, professionals are encouraged to consult resources such as NIST’s official guidelines on identity management and participate in cybersecurity forums and webinars.Challenges of Internal Identity Management* The complexity of Managing Diverse User Roles: Organizations often struggle with the complexity involved in managing diverse user roles and access rights. As companies grow and roles change, keeping track of who has access to what becomes increasingly challenging.* Integration Across Multiple Platforms: Many businesses use various applications and platforms, each with its own identity management controls. Integrating these systems without creating security gaps or user friction is a significant challenge.* Compliance and Regulatory Requirements: Adhering to regulatory requirements for data access and protection, such as GDPR or HIPAA, adds another layer of complexity to identity management. Compliance requires meticulous control and auditing of access rights.* Insider Threats: Managing the risk posed by insider threats is a continuous challenge. Employees with excessive access rights can accidentally or maliciously expose sensitive data.Tips for Improving Internal Identity Management Processes* Regular Audits and Reviews: Regularly audit access rights and user activities. This helps ensure that only the appropriate personnel can access sensitive systems and that any anomalous behavior is quickly detected.* Role-based Access Control (RBAC): Implement role-based access control to minimize access privileges. Users should only have access rights essential to their job functions, reducing the risk of insider threats and data breaches.* Unified Identity Management Solutions: Use a unified identity management system that integrates all user management across various platforms. This improves security and enhances user experience by providing single sign-on (SSO) capabilities.* Multi-factor Authentication (MFA): Enhance security by implementing multi-factor authentication across all systems. MFA adds an extra layer of protection, making it more difficult for unauthorized users to gain access even if they have compromised credentials.Involvement of Other Business Units* Human Resources: HR plays a crucial role in identity management by initiating the user identity setup and termination processes. They ensure the right access is granted when employees join, move within, or leave the company.* IT and Security Teams: These teams implement and maintain the identity management infrastructure. They handle the technical aspects of access controls, audits, compliance, and integrating security measures like MFA.* Compliance and Legal Departments: These units ensure identity management processes comply with relevant laws and regulations. They also help address legal implications related to data breaches or non-compliance.* Departmental Managers: Managers within specific departments must communicate role or employment status changes to HR and IT. They are also responsible for reviewing and approving access requests for their team members, ensuring appropriate access levels.By addressing these challenges and leveraging cross-departmental collaboration, organizations can enhance their identity management practices, strengthening their security posture and compliance with regulatory standards.Actionable and Results-Focused SummaryEfficient and secure management of internal identities is essential in today's digital-first environment, where safeguarding sensitive information and maintaining robust security protocols are paramount. Identity management is vital in authenticating and authorizing individuals within an organization, directly impacting security, compliance, and operational efficiency. Organizations can effectively enhance their security measures by understanding and addressing the complexities involved in managing diverse user roles and integrating multiple platforms.To improve internal identity management processes, organizations should focus on several key actions:* Implement Regular Audits and Reviews: Regular checks on access rights and user activities help maintain security integrity and quickly identify anomalies.* Adopt Role-based Access Control (RBAC): RBAC minimizes access privileges to align with job functions, significantly reducing insider threat risks and potential data breaches.* Utilize Unified Identity Management Solutions: Integrating all user management systems under a single framework enhances security and user experience through single sign-on (SSO) features.* Deploy Multi-factor Authentication (MFA): Strengthening login protocols with MFA ensures an additional layer of security, protecting against unauthorized access even if credentials are compromised.Furthermore, collaboration among various business units—such as Human Resources, IT, Compliance, and Departmental Management—is critical in fostering a secure and compliant identity management framework. HR's role in managing the lifecycle of employee access IT's responsibility for maintaining the identity management infrastructure and Compliance's oversight of regulatory adherence form a comprehensive approach to internal identity management.By effectively addressing these areas, organizations can improve their identity management processes and enhance their overall security posture, ensuring that they remain resilient against emerging cyber threats. This strategic approach to identity management supports the broader goal of safeguarding digital assets while maintaining compliance and operational efficiency.Citation: NIST Cybersecurity Framework (CSF). (n.d.). Framework for Improving Critical Infrastructure Cybersecurity. National Institute of Standards and Technology. https://www.nist.gov/cyberframework This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
11:3905/05/2024

Mastering Shadow IT: Strategies for Integrating Unsanctioned Tech into Your Golden Road Develop
Explore practical strategies to manage and integrate shadow IT into your secured development processes, enhancing security and compliance without stifling innovation. Learn how MSSPs and security consultants can help your business transform shadow IT challenges into assets for growth and security.See post for more detailed write up:https://substack.cpf-coaching.com/p/mastering-shadow-it-strategies This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
17:5701/05/2024

The Pillars of Zero Trust, Trust but Verify feat Chris Foulon & James Azar
Join us live on Fridays at 11 am EST and ask your questions live. If you like a topic covered, send it over to us. The concept of "Trust but verify" within the realm of "Zero Trust" security frameworks is quite intriguing, as it merges a traditional approach to security with a more contemporary, stringent model.Originally, "Trust but verify" was a security principle that emphasized the need for continuous validation. In practice, this means that while organizations might initially trust users or systems, they must consistently verify their credentials and permissions to maintain security. This approach recognizes that trust is essential but must be accompanied by ongoing scrutiny to be effective.On the other hand, "Zero Trust" is a security model based on the philosophy of "never trust, always verify." This model assumes that threats could be internal or external, requiring strict identity verification, strict access controls, and network segmentation to minimize risks. Zero Trust does not inherently trust any entity inside or outside its perimeters at the outset; instead, it demands continuous validation of every request as if it originates from an untrusted source.When we discuss blending "Trust but verify" with "Zero Trust," we look at a nuanced approach that applies rigorous and continuous verification processes in every interaction within an IT environment, regardless of the origin's assumed trustworthiness. This integration helps businesses protect sensitive data and systems by enforcing strict access controls while ensuring that every action is subject to security checks, reducing potential breaches and enhancing overall security posture.For businesses, adopting a "Trust but verify" stance within a zero-trust framework means securing their networks and data more effectively and fostering a culture of security that aligns with dynamic business environments and evolving threat landscapes. This approach ensures that security measures are robust, scalable, and capable of supporting immediate operational needs and long-term strategic goals.When practitioners focus on the "Trust but Verify" pillar within a Zero Trust framework, they should be vigilant about several key aspects that ensure this principle is effectively implemented to safeguard their organization's IT environment. Here are some essential points of concern:* Continuous Verification: Continuous verification is at the heart of the "Trust but Verify" approach. Practitioners need to ensure that verification processes are not just a one-time event but ongoing. This includes re-authenticating users and re-validating their access rights on a regular basis or dynamically based on context, such as changes in user behavior or risk level.* Multi-Factor Authentication (MFA): Implementing MFA is crucial. This security measure adds an extra layer of protection by requiring two or more credentials to verify a user’s identity. Practitioners should ensure these authentication factors are robust and diverse (something you know, something you have, and something you are).* Least Privilege Access Control: Access rights should be tightly controlled and restricted based on the principle of least privilege. This means users are granted only the access necessary to perform their job functions. Practitioners must regularly review and adjust these permissions to adapt to changes in roles and responsibilities.* Audit and Log Review: Regular audits and log reviews are critical for detecting and responding to anomalies and potential security threats. Practitioners should implement automated tools to help monitor and analyze activity logs for unusual actions that could indicate a breach or security risk.* Endpoint Security: With numerous devices accessing the network, securing these endpoints is vital. Practitioners should ensure that all devices are regularly updated, monitored for compliance with security policies, and scanned for vulnerabilities.* Encryption and Data Security: Data should be encrypted at rest and in transit to protect it from unauthorized access. Practitioners must enforce strong encryption standards and regularly update cryptographic keys and protocols to guard against emerging threats.* Segmentation of Network: Network segmentation divides the network into smaller, manageable segments, which can limit the spread of breaches within systems. Practitioners should ensure that these segments are properly secured and that their interactions are monitored to prevent attackers' lateral movement.* User Education and Awareness: Human error often leads to security breaches. Practitioners should invest in regular training programs to keep users aware of security best practices and the latest phishing tactics, thereby reducing the risk of security lapses.* Adaptive Security Policies: Security policies should be adaptable based on context and risk. This includes adjusting access controls based on the user's location, device security posture, and network threats.By concentrating on these points, practitioners can effectively implement the "Trust but Verify" pillar within a zero-trust framework, enhancing their organization's security posture while accommodating the flexibility needed for business operations. This approach strengthens defenses and supports a proactive, resilient security culture.We talked about the course I developed at the end to help students understand the foundations of LLM and prompt engineering. Here is the course for those interested. Join us to unlock the full potential of LLM technology and stay ahead in the competitive landscape. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
30:2719/04/2024

The Pillars of Zero Trust_ Assuming Breach feat Chris Foulon & James Azar
The "Assume Breach" pillar of the Zero Trust model is grounded in the understanding that security breaches are not just possible; they are inevitable. This pragmatic approach dictates that organizations should plan and build their security architectures as if the attackers are already inside their network. Here’s a detailed exploration of the critical strategies under this pillar: 1. Detect and RespondUnder the assumption of a breach, detection, and response capabilities are designed to identify and mitigate threats swiftly before they can cause significant damage. This includes:- Intrusion Detection Systems (IDS): monitor network traffic for suspicious activities and known threats, signaling alerts when potential security breaches are detected.- Security Information and Event Management (SIEM) Systems: SIEM systems collect and aggregate logs from various sources within the network, applying analytics to detect patterns or anomalies that might indicate malicious activity.- Automated Response Solutions: Upon detecting a threat, automated systems can respond immediately by isolating affected segments, blocking malicious communications, or terminating harmful processes, thereby reducing the window of opportunity for attackers to exploit.2. Limit Lateral MovementOnce an attacker gains access to a part of the network, their next goal is often to move laterally to reach valuable data or systems. Strategies to limit this movement include:- Network Segmentation: Dividing the network into smaller, isolated segments or zones can control how traffic moves across the network and limit access to critical assets. Firewalls and access control lists (ACLs) enforce these boundaries by controlling traffic flow based on security policies.- Application Segmentation: Beyond network segmentation, application-level segmentation can further restrict access to applications based on user identity and context, limiting an attacker’s ability to access sensitive applications.- User and Entity Behavior Analytics (UEBA): This technology uses machine learning to understand normal user behavior and can detect deviations that suggest malicious activity, such as an unauthorized attempt to access data. 3. Enhance MonitoringComprehensive monitoring is essential for detecting unusual activities that may indicate a breach. Enhanced monitoring techniques include:- Log Management: Collecting and analyzing logs from all devices and applications across the network provides visibility into activities and potential security incidents.- Endpoint Detection and Response (EDR): EDR tools are deployed on endpoints to monitor and collect data about potentially malicious activities, which can be used to identify and respond to threats.Continuous Monitoring: Continuous monitoring involves the ongoing analysis of security controls and user activities, ensuring that any deviations from the norm can be detected and responded to in real-time.The "Assume Breach" approach shifts the security strategy from merely trying to prevent perimeter attacks to actively managing network security, acknowledging that perfect perimeter defense is unachievable. This mindset encourages continuous improvement of internal controls and rapid response strategies, ultimately strengthening the organization’s resilience against attacks. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
29:5612/04/2024

Podcast - Mastering Vulnerability Management: The Power of Prioritization with EPSS
Discover how EPSS transforms vulnerability management for business leaders, offering strategic insights into cybersecurity's most pressing challenges and future-proof solutions.Originally posted here :https://substack.cpf-coaching.com/p/mastering-vulnerability-management-e45 This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
04:0710/04/2024

Understanding Container Security: Essential Insights for Business Leaders
Audio Version | Discover the critical role of container security in managing vulnerabilities and shaping the future of cybersecurity for business leaders. Gain actionable insights and explore forward-thinking solutions in our guide.Originally posted here: https://substack.cpf-coaching.com/p/understanding-container-security This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
02:3205/04/2024

Two CISOs Talking Cyber Podcast - Zero Trust Security: Least Privilege
Two CISOs Talking Cyber Podcast - Zero Trust Security: Least PrivilegeJames Azar and I discussed the first tenet of Zero Trust Architecture in today’s podcast. I will include additional resources and references for those looking to go deeper down the Rabbit Hole.Previous blogs on the topic from me:NIST SP 800-207 https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-207.pdfSummary:Understanding the principle of Least Privilege is essential for enhancing cybersecurity within an organization. Here's a breakdown of the minimum pros, cons, opportunities, and challenges associated with its use:Pros:* Enhanced Security: By limiting access rights for users to the bare minimum necessary to perform their tasks, the principle of Least Privilege reduces the potential attack surface for cybercriminals.* Reduced Insider Threats: It minimizes the risk of insider threats, whether intentional or accidental, by restricting access to sensitive information and critical systems.* Easier Compliance: Helps organizations comply with regulatory standards and privacy laws by demonstrating that access controls are in place and that data exposure is minimized.Cons:* Implementation Complexity: Setting up Least Privilege access can be complex and time-consuming, requiring a detailed understanding of every user's role and responsibilities.* Potential Productivity Impact: If not managed properly, it could lead to situations where employees are unable to access necessary resources promptly, affecting productivity.* Ongoing Management: Requires continuous monitoring and adjustment as roles change within an organization, adding to administrative overhead.Opportunities:* Improved Security Posture: Implementing Least Privilege can significantly enhance an organization's overall security posture, making it more resilient to attacks.* Cost Savings: By reducing the risk of data breaches, organizations can save on the costs associated with cyber incidents, including fines, remediation efforts, and reputational damage.* Adaptability to Cloud Environments: As more organizations move to cloud-based services, Least Privilege can be efficiently implemented to manage access in these dynamic environments.Challenges:* Determining Access Levels: Accurately defining the access levels required for each user or system can be challenging, especially in complex environments with many interdependent systems and applications.* Resistance from Users: Users accustomed to having broad access may resist the imposition of more restrictive controls, perceiving it as a loss of autonomy or trust.* Keeping Policies Up-to-Date: As organizations evolve, keeping access privileges aligned with current roles and responsibilities requires ongoing vigilance and effort.Incorporating Least Privilege within an organization's security framework presents a balanced set of pros and cons. While it significantly enhances security and compliance, it demands careful planning and continuous management. However, the opportunities it presents for improving an organization's security posture and reducing the risk of data breaches are compelling reasons to overcome these challenges. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
27:4222/03/2024

Unlocking the Power of API Security for Business Success
Fortify Your Digital Frontiers: The Power of API SecurityExplore the critical role of API (Application Programming Interface) security in safeguarding your applications and business. Understand its tasks, challenges, and future solutions through our comprehensive guide designed for business leaders.Originally posted here: https://substack.cpf-coaching.com/p/unlocking-the-power-of-api-security This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
02:4421/03/2024

Secure Your Code, Secure Your Future: The Pillar of Application Security
In an era where digital innovation is king, the integrity of application development processes has never been more critical. At the heart of this digital fortress lies Source Code Supply Chain Security, a linchpin in safeguarding our digital assets against the ever-evolving threats of the cyber world. This introductory dive explores the unseen vulnerabilities within our applications and unveils the paramount importance of securing the very DNA of our software - the source code. As we navigate the complexities of application security, understanding and implementing robust source code supply chain security measures emerge as a basic practice and a necessity in protecting our digital future. Join us as we unravel the layers of protection between your applications and potential adversaries, shedding light on the silent guardians of the digital age. Original article posted here: This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
02:3915/03/2024

Two CISOs Talking Cyber - The Pillars of Zero Trust and Least Privilege: featuring Chris Foulon and James Azar
The conversation, hosted by James Azar on the Cyber Hub Podcast, delves into the concepts of zero trust and least privilege in cybersecurity. With contributions from speakers including Chris Foulon, they explore the multifaceted approach to access and data management within the framework of zero trust, providing insights into practical implementation and the underlying philosophy guiding these principles.Main Points:* Concept and Importance of Least Privilege: The discussion highlights least privilege as a critical aspect of cybersecurity, emphasizing its role beyond mere access management. It's portrayed as a comprehensive framework that includes access, availability, data classification, and understanding, ensuring individuals access the necessary resources and information precisely when needed, thereby enhancing security and efficiency.* Implementation Challenges and Strategies: Speakers touch upon the practical challenges of implementing least privilege, including the need for a nuanced understanding of business operations and the role of security in enabling business objectives. They discuss the importance of balancing security measures with business productivity, avoiding overly restrictive practices that may hinder operational efficiency or encourage circumvention of security protocols.* Evolution of Access Management: The conversation also covers the evolution of access management towards automation and just-in-time access, reflecting on the advancements in technology that enable more dynamic, context-sensitive, and efficient control over access rights. This approach facilitates the application of least privilege principles by granting access based on immediate need, thereby reducing the risk of excessive privileges accumulating over time.The podcast provides a deep dive into the principles of least privilege and zero trust, illustrating their significance in contemporary cybersecurity practices. It underscores the balance required between enforcing robust security measures and supporting the operational needs of a business, all while adapting to the evolving landscape of threats and technological advancements. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
27:4208/03/2024

What do CISO’s Really think of NIST CSF 2.0 featuring Chris Foulon and James Azar Exploring NIST CSF 2.0: A Fresh Perspective on Cybersecurity Frameworks
Co-produced with James Azar - Exploring NIST CSF 2.0: A Fresh Perspective on Cybersecurity Frameworks A Dive into the Enhanced NIST Cybersecurity Framework This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
29:2401/03/2024

Embracing Evolution: Navigating the Shift from NIST CSF 1.0 to 2.0
Introduction to NIST Cybersecurity Framework (CSF)Before exploring the changes, let's understand the NIST Cybersecurity Framework. Consider it a comprehensive guide for organizations to manage cybersecurity risks. Like a detailed map that helps you navigate an unknown city, the NIST CSF helps organizations navigate the complex landscape of cybersecurity threats and practices.Transitioning from NIST CSF 1.0 to 2.0Expanding on the specific changes introduced in NIST CSF 2.0 provides a clearer picture of how the framework has evolved to address the dynamic landscape of cybersecurity threats and the increasing importance of privacy.The changes introduced in NIST CSF 2.0 reflect a natural evolution of the framework in response to the ever-changing cybersecurity landscape. By incorporating privacy considerations, emphasizing supply chain security, clarifying language, offering customization, and aligning with other NIST publications, the updated framework aims to provide organizations with a more effective, flexible, and comprehensive tool for managing cybersecurity risks.For business stakeholders, understanding these specific changes is crucial for effectively leveraging the NIST CSF to enhance their organization's cybersecurity posture. Implementing the updated practices and principles of NIST CSF 2.0 can help organizations protect against evolving cyber threats, ensure personal data privacy, and foster a resilient and secure digital environment.Originally posted: https://substack.cpf-coaching.com/p/csf-2 This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
07:5101/03/2024

Is Zero Trust a Buzzword or something SMBs can implement?
Imagine your business as a modern-day fortress in an era of digital warfare, where threats don't march in broad daylight but lurk in the shadows of the digital world. Traditional moats and walls (perimeter-based security) are no longer sufficient in this landscape. Enter Zero Trust is a strategy not just of defense but of intelligent, dynamic warfare against cyber threats. This blog post deciphers the principles and tenants of Zero Trust, transforming them into a blueprint for constructing an impregnable digital fortress.Cybersecurity Leadership Development Coaching | CPF Coaching is a reader-supported publication. To receive new posts and support my work, consider becoming a free or paid subscriber.Originally posted: This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
03:4624/02/2024

Zero Trust Done Right with James Azar & Christophe Foulon
Lists of books mentionedStart-Up Secure: Baking Cybersecurity into Your Company from Founding to Exit https://www.amazon.com/Start-Up-Secure-Cybersecurity-Company-Founding/dp/1119700736Project Zero Trust: A Story About a Strategy for Aligning Security and the Business https://www.amazon.com/Project-Zero-Trust-Strategy-Aligning/dp/B0BG6D1J26/A Data-Driven Computer Defense: THE Computer Defense You Should Be Using https://www.amazon.com/Data-Driven-Computer-Defense-Should-Using/dp/B0BR9KS3ZF/ This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
29:3423/02/2024

Maximizing Application Security with OSS
Discover the critical importance of inventorying open-source components in your application security program. Learn how this practice can safeguard your business from vulnerabilities and enhance your software's integrity. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
03:5020/02/2024

Breaking into Cybersecurity Leadership Roselle Safran
Thank you for reading Cybersecurity Leadership Development Coaching | CPF Coaching. This post is public, so feel free to share it.Breaking into Cybersecurity Leadership Roselle SafranRoselle Safran on LinkedIn https://www.linkedin.com/in/rosellesafran/Sponsored by CPF Coaching LLC - http://cpf-coaching.comThe Breaking into Cybersecurity: It’s a conversation about what they did before, why did they pivot into cyber, what the process was they went through Breaking Into Cybersecurity, how they keep up, and advice/tips/tricks along the way.The Breaking into Cybersecurity Leadership Series is an additional series focused on cybersecurity leadership and hearing directly from different leaders in cybersecurity (high and low) on what it takes to be a successful leader. We focus on the skills and competencies associated with cybersecurity leadership and tips/tricks/advice from cybersecurity leaders.This podcast runs on listener support and funding. Consider supporting this podcast:https://breaking-into-cybersecurity.captivate.fm/supportCheck out our books:Develop Your Cybersecurity Career Path: How to Break into Cybersecurity at Any Level: https://amzn.to/3443AUI Hack the Cybersecurity Interview: A complete interview preparation guide for jumpstarting your cybersecurity career https://www.amazon.com/dp/1801816638/About the hosts:Renee Small is the CEO of Cyber Human Capital, one of the leading human resources business partners in the field of cybersecurity, and author of the Amazon #1 best-selling book, Magnetic Hiring: Your Company's Secret Weapon to Attracting Top Cyber Security Talent. She is committed to helping leaders close the cybersecurity talent gap by hiring from within and helping more people get into the lucrative cybersecurity profession. https://www.linkedin.com/in/reneebrownsmall/ Download a free copy of her book at magnetichiring.com/bookChristophe Foulon focuses on helping to secure people and processes with a solid understanding of the technology involved. He has over ten years of experience as an experienced Information Security Manager and Cybersecurity Strategist with a passion for customer service, process improvement, and information security. He has significant experience in optimizing the use of technology while balancing the implications to people, processes, and information security by using a consultative approach.https://www.linkedin.com/in/christophefoulon/Find out more about CPF-Coaching at https://www.cpf-coaching.com* Website: https://www.cyberhubpodcast.com/breakingintocybersecurity* Podcast: https://feeds.captivate.fm/breaking-into-cybersecurity/* YouTube: https://www.youtube.com/c/BreakingIntoCybersecurity* Linkedin: https://www.linkedin.com/company/breaking-into-cybersecurity/* Twitter: https://twitter.com/BreakintoCyber* Twitch: https://www.twitch.tv/breakingintocybersecurity This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
28:1516/02/2024

The Strategic Imperative of Application Security Integration into the SDLC and Project Delivery The Strategic Imperative of Application Security Integration into the SDLC and Project Delivery
In the dynamic realm of digital transformation, integrating application security into the Software Development Life Cycle (SDLC) and project delivery has emerged as a pivotal strategy for businesses aiming to navigate the complexities of the modern cybersecurity landscape. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
03:3012/02/2024

Enhancing Application Security: A Deep Dive into OWASP and SANS Top 10 Training and Review
Step up your application security game! Our latest blog explores how training and reviewing with OWASP & SANS Top 10 can make a difference. #ApplicationSecurity #OWASP #SANSTop10This expanded blog post provides a more in-depth look at the significance of training and review in application security, specifically through the lens of the OWASP and SANS Top 10. It aims to educate and motivate a broad range of stakeholders to adopt these practices for enhanced security.This podcast runs on listener support and funding. Consider supporting this podcast:https://breaking-into-cybersecurity.captivate.fm/supportCheck out our books: Develop Your Cybersecurity Career Path: How to Break into Cybersecurity at Any Level: https://amzn.to/3443AUIHack the Cybersecurity Interview: A complete interview preparation guide for jumpstarting your cybersecurity career https://www.amazon.com/dp/1801816638/_________________________________________About the hosts: Christophe Foulon focuses on helping to secure people and processes with a solid understanding of the technology involved. He has over ten years of experience as an experienced Information Security Manager and Cybersecurity Strategist with a passion for customer service, process improvement, and information security. He has significant experience in optimizing the use of technology while balancing the implications to people, processes, and information security by using a consultative approach.https://www.linkedin.com/in/christophefoulon/Find out more about CPF-Coaching at https://www.cpf-coaching.com- Website: https://www.cyberhubpodcast.com/breakingintocybersecurity- Podcast: https://feeds.captivate.fm/breaking-into-cybersecurity/- YouTube: https://www.youtube.com/c/BreakingIntoCybersecurity- Linkedin: https://www.linkedin.com/company/breaking-into-cybersecurity/- Twitter: https://twitter.com/BreakintoCyber- Twitch: https://www.twitch.tv/breakingintocybersecurity This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
03:4626/01/2024

Insights into the CISO MindMap - Mastering Vulnerabilities: Elevating Business Security with a Priority Focused Approach
Dive deep into vulnerability classification, and learn why a Priority Focused Approach is a game-changer for business cybersecurity in the digital era. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
03:5315/09/2023

The Power of Identification in Continuous Vulnerability Management
Uncover the significance of identification in periodic vulnerability management. Stay updated on current challenges and future-forward solutions to safeguard your digital assets.Diving into the CISO Mindmap - A series providing increased clarity into the role of a CISOI wanted to pay homage to the work of Rafeeq Rehman and the CISO Mind Map https://rafeeqrehman.com/2023/03/25/ciso-mindmap-2023-what-do-infosec-professionals-really-do/ so with the approval of Rafeeq; I will take an overview or summary of the different areas. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
04:0228/08/2023

Strengthening Your Armor_ A Guide to Effective Vulnerability Management
As a business leader, ensuring a secure digital environment is crucial. Our latest blog post covers the importance of vulnerability management, offering insights into identification tasks, environmental challenges, and forward-looking solutions. Stay ahead of the curve! #Cybersecurity #VulnerabilityManagement This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
04:5925/08/2023

Unveiling Cybersecurity's Secret Weapon_ A Deep Dive into Identification in Comprehensive Vulnerability Management
The Indispensable Role of Identification in Comprehensive Vulnerability Management: In-depth Insights for Modern Business LeadersDiving into the CISO Mindmap - A series providing increased clarity into the role of a CISOI wanted to pay homage to the work of Rafeeq Rehman and the CISO Mind Map https://rafeeqrehman.com/2023/03/25/ciso-mindmap-2023-what-do-infosec-professionals-really-do/ so with the approval of Rafeeq; I will take an overview or summary of the different areas. Unearth the essential function of identification within comprehensive vulnerability management, the associated tasks, present environmental challenges, and innovative future solutions. Equip your business with practical strategies and action plans to bolster your cybersecurity preparedness.Posted: https://substack.cpf-coaching.com This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
04:2924/08/2023

Navigating the Cyber Landscape: IoT Vulnerability Management, Challenges and Solutions
Navigating the Cyber Landscape: IoT Vulnerability Management, Challenges and SolutionsUncover the scope of IoT in vulnerability management.I wanted to pay homage to the work of Rafeeq Rehman and the CISO Mind Map https://rafeeqrehman.com/2023/03/25/ciso-mindmap-2023-what-do-infosec-professionals-really-do/ so with the approval of Rafeeq; I will take an overview or summary of the different areas. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
04:1404/07/2023

Optimizing Security: The Importance of Scoping Network Devices in Your Vulnerability Management Program
This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
03:4914/06/2023

Navigating Vulnerability Management_ Scoping Operating Systems for a Secure Business Future
This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
03:0113/06/2023

Insights into the CISO Mind Map — Vulnerability Management
Diving into the CISO Mindmap - A series providing increased clarity into the role of a CISOI wanted to pay homage to the work of Rafeeq Rehman and the CISO Mind Map https://rafeeqrehman.com/2023/03/25/ciso-mindmap-2023-what-do-infosec-professionals-really-do/ so with the approval of Rafeeq; I will take an overview or summary of the different areas.Posted: Extreme Productivity, by Robert C. PozenAt some point, we’ve all asked ourselves “Where can I get more time to do the things I want to do?” The answer, from Robert C. Pozen, is found in his fascinating new book Extreme Productivity.Click here to view this summary.If you have read this far into my blog, I pick you as a continuous learner. Amy right? I know I am!Check out this new leadership and soft skill development approach called Social Nano Learning.It has been proven to increase team engagement, learning outcomes, and psychological well-being in only 3 minutes daily.I’ve partnered with NanoCourses and can offer you and your team your first NanoCourse (based on the 7 Habits of Highly Effective People) free of charge.There’s a quick 3-minute video describing exactly what NanoCourses is, and how you can get started, here:www.nancourses.io/cpf-coaching-partners This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
04:3503/06/2023

Insights into the CISO Mindmap - Network/Application Firewalls
This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
06:0303/06/2023

Diving into the CISO Mindmap - Security Operations Resilience
This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
05:3703/06/2023

Insights into the CISO Mind Map - Threat Prevention (NIST CSF Identify & Protect)
This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
04:0503/06/2023

Navigating Remote Networking as a Cybersecurity Leader
Also shared on MediumCybersecurity Leadership Development Coaching | CPF Coaching is a reader-supported publication. Support authors by subscribing and supporting the community. To receive new posts and support my work, consider becoming a free or paid subscriber.Book of the WeekRemote Work Revolution, by Tsedal NeeleyUncover the secrets to successfully navigating remote work, boosting productivity, fostering collaboration, and unlocking the full potential of your team in a virtual environment.Click here to view this summary. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
03:4828/05/2023
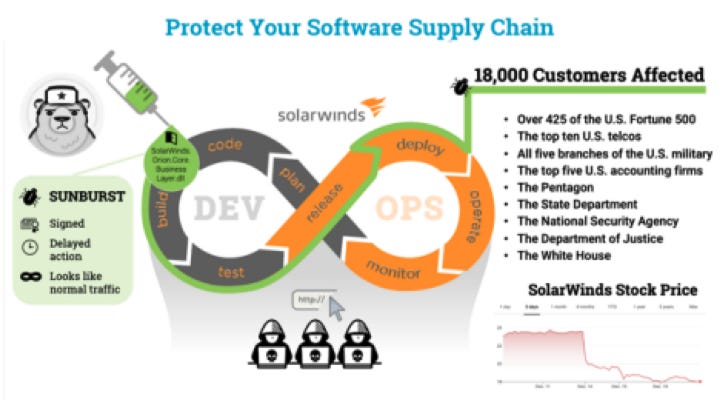
Understanding your digital supply chain risk
Originally published here: https://www.capitalone.com/tech/cloud/understanding-your-digital-supply-chain-risk/ RemovedUnderstanding your digital supply chain riskManaging the risks associated with digital supply chainsTL;DRUnderstanding your digital supply chain risk is becoming one of the major challenges many businesses face today, especially with the move to cloud and globalization of the computing behind those services. Recommendations on addressing the additional detailing of the supply chain which might be part of any major applications* Ensure that COTS/Third Party Suppliers/SaaS are documented on the security context diagram, threat model, CMDB and any other sources of record, as well as potential platforms which might support them as part of their digital supply chain * Ensuring that these dependencies are captured will help to better identify supply chain risks, threat model potential mitigations for them, as well as a myriad of other detection and response activities What are digital supply chain risks?As companies move to the cloud and computing becomes globalized, it is important to understand your digital supply chain risk and how to mitigate the risks. Risks we will discuss today include gaps in: * Cyber architecture requirements * Change management databases (CMDB)* Software supply chain & software development lifecycles * Supply chain risk management processHow does supply chain risk affect businesses?An organization’s understanding of the supply chain risk of any given system can range in varying degrees based on the number of integrators or suppliers a company might use to generate its revenue through the production of software or delivery of services. In addition to understanding those integrators or suppliers, understanding the external factors which might affect them, and in-turn affect the producer. An organization’s ability to identify, detect and respond to those environmental threats/influences to the supply chain become a critical factor in maintaining the integrity of the production of software and services. An organization’s Third Party Management (TPM) program helps monitor its Third Parties. This program also helps with the lifecycle management of suppliers while servicing the Organization. Due to the complexity of an organization's supply chain, there might be multiple layers of suppliers or intermediaries downstream of the organization. As the layers of downstream supplier’s increase, Organization’s ability to have visibility into those suppliers decreases.In the figure below from NIST SP 800-161r1 demonstrate the decreased invisibility as the layers of the supply chain increase.This blog focuses on the digital supply chain risks which affect organizations. Risk #1: Gaps in cyber architecture requirements What is the risk associated with cyber architecture?Organizations might not document or track 3rd parties/supplier chain infrastructure as part of its supply chain in its Change Management Database (CMDB) and it is not a requirement for it to be completed.Why does the gap in cyber architecture matter? This means that the Organization might not be able to proactively respond to major vulnerabilities in our supply chain which have been integrated or used to build organizations products on. (e.g. Log4J)What is a potential mitigation? Having the ability to understand the technologies used to support solutions by our critical suppliers and have them linked as an artifact in CMDB and TPM. This will provide the organization with the ability to proactively understand the risk exposure from suppliers.Risk #2: Gaps in Change Management Databases (CMDB)Oftentimes, companies do not connect their suppliers or third party applications in CMDB to the authoritative system of record for TPM, therefore understanding the digital supply chain risks caused by those third parties to the applications that they support. The probable impact of gaps in CMDBThis has the potential to limit an organization's ability to proactively respond to major vulnerabilities in the supply chain which have been integrated or used to build organization products on. The potential mitigation of gaps in CMDB Require understanding of the technologies used to support solutions by our critical suppliers and have them linked as an artifact in CMDB and TPM. This aDolus blog includes a diagram demonstrating a software supply chain attack. Risk #3: Gaps in software supply chain and software development lifecycles Currently, an organization has a potential lack of/limited visibility into some of the software libraries ingested from software providers, open source software, etc. Take Log4j as an example. The Black Kite Research Team analyzed nearly 3,000 companies known to be affected or explicitly disclosed to be unaffected by the vulnerability, as shown int he figure below.Potential mitigations of software supply chain and software development lifecycles One of the potential mitigations for increased visibility into the software libraries ingested from software providers, open source software, etc. is the Software Bill of Materials. With a Software Bill of Materials (SBOM), you can respond quickly to the security, license and operational risks that come with open source use. This could also be potentially used to track the integration of Commercial Off the Shelf (COTS) Software into organization business applications groups. Below is a software lifecycle. Also, check out National Institute of Standards and Technology (NITA)’s illustration of a software lifecycle and SBOM.The use of the software bill of materials concept can even be expanded to include firmware down at the hardware level. There has been an increase in organizations adopting SBOM as part of their supply chain, as well as future regulator requirements from the federal government. Industry resources for SBOMs: In May 2022, President Biden issued an executive order advocating for mandatory software bills of materials, or SBOM, to increase software transparency and counter supply-chain attacks. Some examples of these include:* CycloneDX SBOM * NITA SBOM, formats and tooling* Jupiter One SBOM* Google Supply-Chain Levels for Software Artifacts (SLSA) framework * NSA recommended practices for developers to secure the software supply chainRisk #4: Gaps in the supply chain risk management process An organization’s third-party applications which might in CMDB are not linked to/associated with the authoritative system of record for third party relationships (TPM Central) (e.g., Solarwinds, VMware, Microsoft, etc). Potential mitigation of supply chain risk management process It is also recommended that there should be an integration implemented between CMDB and the TPM system of record to organize/document the relationship between business applications and third party records/engagements. This will allow for TPM and other downstream groups to consume this information from systems of record CMDB when needed. Industry resources for supply chain risk management NIST’s Computer Security Resource Center (CSRC) offers this Cybersecurity Supply Chain Risk Management C-SCRM.Enterprise’s supply chain Contemporary enterprises run complex information systems and networks to support their missions. These information systems and networks comprise ICT/OT products and components made available by suppliers, developers, and system integrators. Enterprises also acquire and deploy an array of products and services, including: * Custom software for information systems built to be deployed within the enterprise, made available by developers; * Operations, maintenance, and disposal support for information systems and networks within and outside of the enterprise’s boundaries, made available by system integrators or other ICT/OT-related service providers; and * External services to support the enterprise’s operations are positioned both inside and outside the authorization boundaries, and made available by external system service providers. Below are some additional resources: * CSA SaaS Governance and Security Best Practices* Cybersecurity Supply Chain Risk Management C-SCRM* NIST SP 800-161 R1* Key Practices in Cyber Supply Chain Risk Management:Observations from Industry* MITRE Systems of Trust This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
08:2709/04/2023
Developing cybersecurity leadership talent pipelines
This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
01:1909/04/2023

The Top 10 LinkedIn Security Tips: Leaderboards are no longer just in the office
Section 1: Understand the RisksAs a cybersecurity professional, you understand the importance of protecting sensitive information. However, it’s essential to understand the specific risks associated with LinkedIn. For example, hackers often use LinkedIn to gather information for social engineering attacks. Be aware of the risks and take steps to mitigate them.One way to do this is to limit your personal information on LinkedIn. Don’t include sensitive details like your home address or phone number. Also, be cautious about what you post in your profile or status updates. Avoid sharing information that could be used to guess your security questions, like your mother’s maiden name or your first pet’s name.Finally, be aware of phishing scams. Hackers may send you messages on LinkedIn that look legitimate but contain malware or links to fake login pages. Double-check the sender’s email address and verify any links before clicking on them.Section 2: Secure Your AccountThe first step to securing your LinkedIn account is to enable two-factor authentication (2FA). This adds an extra layer of security by requiring a code and your password to log in. LinkedIn offers several 2FA options, including SMS messages, phone calls, and authentication apps like Google Authenticator.It would be best if you also chose a strong, unique password for your LinkedIn account. Avoid using the same password for multiple accounts, and use a combination of letters, numbers, and symbols to make your password more secure.Finally, keep your account up-to-date by regularly reviewing your security settings and checking for suspicious activity.Section 3: Be Mindful of Your ConnectionsLinkedIn is designed to help you connect with other professionals, but it’s essential to be mindful of who you connect with. Before accepting a connection request, please take a few minutes to review the person’s profile and confirm that they are who they say they are.Additionally, be cautious about accepting requests from people you don’t know. Hackers often use fake LinkedIn profiles to gather information or spread malware. If you’re unsure about a connection request, it’s better to err on caution and decline it.Finally, be careful about what you share with your connections. Don’t post sensitive information or business secrets; be cautious about sharing personal details like your home address or phone number.Section 4: Keep Your Profile SecureYour LinkedIn profile is a valuable source of information for hackers, so it’s essential to keep it secure. One way to do this is to limit the information you share. For example, think about when you might share or add to your entire work history or include your phone number.Be cautious about what you post on your profile. Avoid sharing information that could be used to guess your security questions, like your mother’s maiden name or your first pet’s name.Finally, you can set your profile to private if you’re not actively looking for a job. This will prevent recruiters and others from seeing your profile and potentially using your information for phishing scams or other attacks.Section 5: Monitor Your ActivityMonitoring your LinkedIn activity regularly is essential to ensure your account hasn’t been compromised. Check your login history and review any changes to your profile or connections.If you notice any suspicious activity, such as logins from unfamiliar locations or changes to your profile that you didn’t make, take immediate action. Change your password, review your security settings, and contact LinkedIn support if necessary.Additionally, be on the lookout for phishing scams or other suspicious messages. If you receive a message that seems too good to be accurate or asks for sensitive information, it’s likely a scam.Section 6: Use LinkedIn Safely on Public Wi-FiPublic Wi-Fi networks often need to be more secure, which means that hackers can easily intercept your data if you’re not careful. To stay safe using LinkedIn on public Wi-Fi, ensure you use a secure connection. Consider using a virtual private network (VPN) to encrypt your data and protect your privacy.Additionally, be cautious about using public computers to access LinkedIn. Use your device and make sure it’s secure before logging in.Finally, be mindful of who is watching you when using LinkedIn in public. Don’t type in sensitive information if people nearby could see your screen.Section 7: Keep Your LinkedIn App Up-to-DateIf you use the LinkedIn app on your smartphone or tablet, it’s essential to keep it up-to-date. App updates often include security patches that can help protect your data and prevent attacks.Additionally, be cautious about downloading apps from third-party sources. Stick to official app stores like the Apple App Store or Google Play Store to reduce the risk of downloading malware or other malicious apps.Finally, be careful about the permissions you grant to apps on your device. Don’t grant unnecessary permissions, and be cautious about giving access to your contacts or other sensitive information.Section 8: Use LinkedIn Learning SafelyLinkedIn Learning is a valuable resource for cybersecurity professionals, but it’s essential to use it safely. Be cautious when downloading course materials or other files: Ensure you’re downloading files from trusted sources and scan them for viruses or malware before opening them.Section 9: Protect Your Company’s InformationIf you’re a cybersecurity professional working for a company, protecting your company’s information on LinkedIn is essential. Ensure your employees know the risks associated with LinkedIn and train them on best practices for using the platform safely.Additionally, consider setting up a company page on LinkedIn to control the information shared about your company. Review your employees’ profiles to ensure they’re not sharing sensitive information, and monitor your company’s activity on the platform regularly.Finally, be cautious about sharing information about your company’s products or services on LinkedIn. Don’t post sensitive information or business secrets, and be careful about sharing personal details like your home address or phone number.Section 10: Be Prepared for a Data BreachEven if you take all the necessary precautions, there’s always a risk of a data breach. Be prepared by having a plan in place for responding to a violation.Make sure you know who to contact in the event of a breach, and have a plan for notifying affected individuals and authorities if necessary. Consider working with a cybersecurity firm to help you respond to breaking and minimize the damage.Finally, review your insurance policies to ensure adequate coverage in a breach. Cyber insurance can help cover the costs associated with a breach, including legal fees, notification costs, and damage to your reputation.Summing it all upIn conclusion, LinkedIn can be a valuable resource for professionals, but it’s also important to be mindful of the security risks associated with the platform. By following these top 10 security tips, including understanding the risks, securing your account, being aware of your connections, keeping your profile secure, monitoring your activity, using LinkedIn safely on public Wi-Fi, keeping your LinkedIn app up-to-date, using LinkedIn Learning safely, and protecting your company’s information, you can stay ahead of the cybersecurity game and help ensure that your personal and professional information remains secure. By taking these simple precautions, you can enjoy all the benefits of LinkedIn without putting yourself or your company at risk of cyberattacks. This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
07:2118/03/2023

The Digital Risk Digest Live Feat. Christophe Foulon
The Digital Risk Digest Live Feat. Christophe Foulon By https://www.youtube.com/@valor-cybersecurity Welcome to another episode of the Digital Risk Digest Live. We go live every Friday with industry leaders about digital threats, opportunities, and more. Curious about the intersection of business and technology? Tune in today! Let’s give Chris a massive welcome to the show! This is a public episode. If you’d like to discuss this with other subscribers or get access to bonus episodes, visit substack.cpf-coaching.com/subscribe
01:00:1419/02/2023





